A new Android malware named ‘FireScam’ is being distributed as a premium version of the Telegram app via phishing websites on GitHub that mimick the RuStore, Russia's app market for mobile devices.
RuStore launched in May 2022 by the Russian internet group VK (VKontakte) as an alternative to Google Play and Apple’s App Store, following Western sanctions that impacted Russian users’ access to mobile software.
It hosts apps that are compliant with Russian regulations and it was created with the support of the Russian Ministry of Digital Development.
According to researchers at threat management company Cyfirma, the malicious GitHub page mimicking RuStore first delivers a dropper module called GetAppsRu.apk.
The dropper APK is obfuscated using DexGuard to evade detection and acquires permissions that allow it to identify installed apps, gives it access to the device’s storage, and install additional packages.
Next, it extracts and installs the main malware payload, ‘Telegram Premium.apk’, which requests permissions to monitor notifications, clipboard data, SMS, and telephony services, among others.

RuStore clone hosted on a GitHub.io domain
FireScam capabilities
Upon execution, a deceptive WebView screen showing a Telegram login page steals the user’s credentials for the messaging service.
FireScam establishes communication with a Firebase Realtime Database where it uploads stolen data in real-time and registers the compromised device with unique identifiers, for tracking purposes.
Cyfirma
http://www.cyfirma.com/research/insi...-capabilities/ that stolen data is only stored in the database temporarily and then wiped, presumably after the threat actors filtered it for valuable information and copied it to a different location.
The malware also opens a persistent WebSocket connection with the Firebase C2 endpoint for real-time command execution like requesting specific data, triggering immediate uploads to the Firebase database, downloading and executing additional payloads, or adjusting the surveillance parameters.
FireScam can also monitor changes in the screen activity, capturing on/off events and log the active app at the time as well as activity data for events lasting for more than 1,000 milliseconds.
The malware also meticulously monitors any e-commerce transactions, attempting to capture sensitive financial data.
Anything the user types, drags and drops, copies to clipboard, and intercepts even data automatically filled from password managers or exchanges between apps, categorized, and exfiltrated to the threat actors.
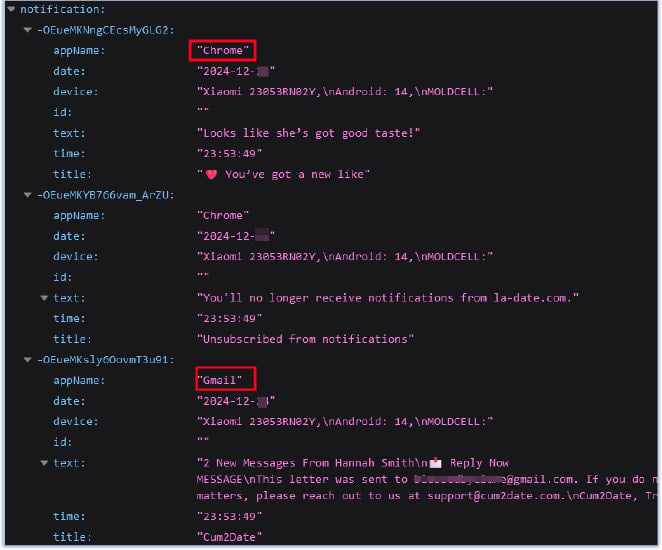
Data exfiltrated by FireScam
Although Cyfirma does not have any hints pointing to FireScam's operators, the researchers say that the malware is a "sophisticated and multifaceted threat" that "employs advanced evasion techniques."
The company recommends users to execute caution when opening files from potentially untrusted sources or when clicking on unfamiliar links.
https://www.bleepingcomputer.com/new...m-premium-app/

