Ten npm packages were suddenly updated with malicious code yesterday to steal environment variables and other sensitive data from developers' systems.
The campaign targeted multiple cryptocurrency-related packages, and the popular 'country-currency-map' package was downloaded thousands of times a week.
The malicious code was discovered by Sonatype researcher Ali ElShakankiry and is found in two heavily obfuscated scripts, "/scripts/launch.js" and "/scripts/diagnostic-report.js," which execute upon the package installation.
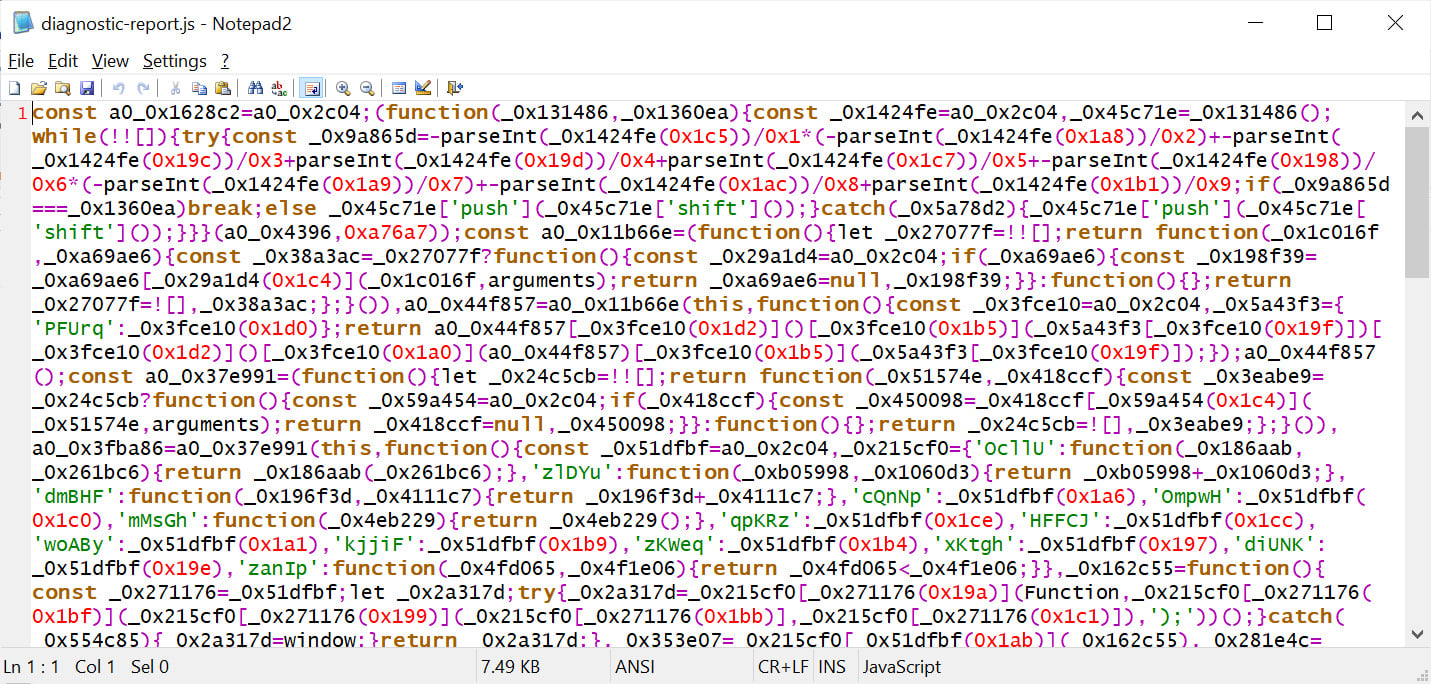
Malicious diagnostic-report.js script
Sonatype says that the JavaScript steals the device's environment variables and sends them to the remote host "eoi2ectd5a5tn1h.m.pipedream(.)net)". Environment variables are commonly targeted as they can contain API keys, database credentials, cloud credentials, and encryption keys, which can be used for further attacks.
Malicious code introduced via update
As Sonatype malware analyst and fellow BleepingComputer reporter Ax Sharma explains in a write-up, as the malicious code is the same in all of the repositories and most have had a clean record for years, they were likely compromised in some manner.
"We hypothesize the cause of the hijack to be old npm maintainer accounts getting compromised either via credential stuffing (which is where threat actors retry usernames and passwords leaked in previous breaches to compromise accounts on other websites), or an expired domain takeover — both common scenarios explained in npm documentation,"
https://www.sonatype.com/blog/multip...-info-stealers.
"Given the concurrent timing of the attacks on multiple packages from distinct maintainers, the first scenario (maintainer accounts takeover) appears to be a more likely scenario as opposed to well-orchestrated phishing attacks."
The package names, their compromised versions, and how many times the malicious version was download are listed below:
- country-currency-map: version 2.1.8, 288 downloads.
- @keepkey/device-protocol: version 7.13.3, 56 downloads.
- bnb-javascript-sdk-nobroadcast: version 2.16.16, 61 downloads.
- @bithighlander/bitcoin-cash-js-lib: version 5.2.2, 61 downloads.
- eslint-config-travix: version 6.3.1, 0 downloads.
- babel-preset-travix: version 1.2.1, 0 downloads.
- @travix/ui-themes: version 1.1.5, 0 downloads.
- @veniceswap/uikit: version 0.65.34, 0 downloads.
- @crosswise-finance1/sdk-v2: version 0.1.21, 0 downloads.
- @veniceswap/eslint-config-pancake: version 1.6.2, 0 downloads.
All these packages, except for country-currency-map, are still available on npm, with their latest versions designated above, so downloading them will infect your projects with info-stealer malware.
The
https://www.npmjs.com/package/country-currency-map package maintainer deprecated the malicious version (2.1.8) yesterday and left a note telling developers to use version 2.1.7 instead, which is safe.
.jpg)
Maintainer's notice on npm
The hypothesis that the attack was caused by poor npm maintainer account security is further supported by the fact that the corresponding GitHub repositories of the compromised projects were not updated with malware.
Although npm has made two-factor authentication mandatory for popular projects, some of those impacted by the latest campaign are older packages with their last update several years ago. Hence, their maintainers may no longer be actively involved.
https://www.bleepingcomputer.com/new...-targets-devs/

