Oracle finally confirmed in email notifications sent to customers that a hacker stole and leaked credentials that were stolen from what it described as "two obsolete servers."
However, the company added that its Oracle Cloud servers were not compromised, and this incident did not impact customer data and cloud services.
"Oracle would like to state unequivocally that the Oracle Cloud—also known as Oracle Cloud Infrastructure or OCI—has NOT experienced a security breach," Oracle says in a customer notification shared with BleepingComputer.
"No OCI customer environment has been penetrated. No OCI customer data has been viewed or stolen. No OCI service has been interrupted or compromised in any way," it added in emails sent from
mailto:[email protected], prompting customers to contact Oracle Support or their account manager if they have additional questions.
"A hacker did access and publish user names from two obsolete servers that were never a part of OCI. The hacker did not expose usable passwords because the passwords on those two servers were either encrypted and/or hashed. Therefore the hacker was not able to access any customer environments or customer data."

Oracle email statement
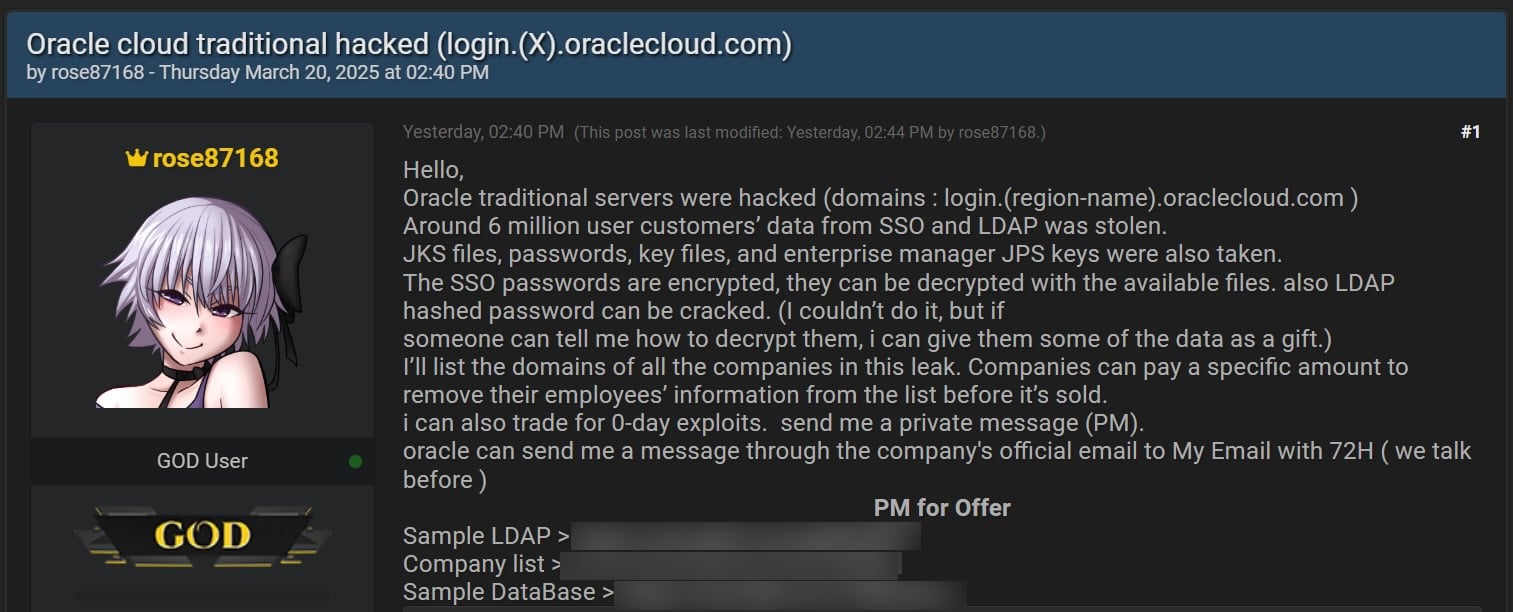
Since the incident surfaced in March, when a threat actor (rose87168)
https://www.bleepingcomputer.com/new...-data-records/ for sale on BreachForums, Oracle has consistently denied reports of an Oracle Cloud breach in statements shared with the press. While this is admittedly true as it matches what Oracle is telling customers—that the breach impacted an older platform, Oracle Cloud Classic—this is merely wordsmithing, as
http://doublepulsar.com/oracle-attem...e-9231c8daff4a.
"Oracle rebadged old Oracle Cloud services to be Oracle Classic. Oracle Classic has the security incident," Beaumont said. "Oracle are denying it on 'Oracle Cloud' by using this scope — but it's still Oracle cloud services that Oracle manage. That's part of the wordplay."
BleepingComputer has contacted Oracle to confirm whether these notices are legitimate and not sent by the threat actor or another third party, but we haven't received a response. Oracle has also yet to clarify if the breached servers are part of Oracle Cloud Classic or another platform.
Data allegedly stolen from Oracle Cloud up for sale
The breach that wasn't a breach
This comes after the company
https://www.bleepingcomputer.com/new...-to-customers/ in calls with some of its clients one week ago that attackers stole old client credentials after breaching a "legacy environment" last used in 2017.
However, while Oracle told customers that this was non-sensitive old legacy data, the threat actor behind the breach shared data with BleepingComputer from the end of 2024 and later posted newer records from 2025 on BreachForums.
https://www.bleepingcomputer.com/new...each-is-valid/ with multiple Oracle customers that samples of the leaked data (including associated LDAP display names, email addresses, given names, and other identifying information) received from the threat actor were valid after
https://www.bleepingcomputer.com/new...-data-records/ that "There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data."
Cybersecurity firm
https://cybelangel.com/oracle-data-leak-breaking-news/ first revealed last week that Oracle told customers that an attacker deployed a web shell and additional malware on some of Oracle's Gen 1 (also known as Oracle Cloud Classic) servers as early as January 2025. Until the breach was detected in late February, the threat actor allegedly stole data from the Oracle Identity Manager (IDM) database, including user emails, hashed passwords, and usernames.
Last month, BleepingComputer first reported that Oracle privately notified customers of another
https://www.bleepingcomputer.com/new...-us-hospitals/ (a software-as-a-service (SaaS) company previously known as Cerner), which impacted patient data at multiple healthcare organizations and hospitals in the United States.
Sources told BleepingComputer that a threat actor named "Andrew"—who has yet to claim affiliation with an extortion or ransomware operation—is now extorting the breached hospitals, demanding millions of dollars in cryptocurrency not to sell or leak the stolen data.
https://www.bleepingcomputer.com/new...-cloud-breach/

