
Cybercrime marketplaces are increasingly selling stolen corporate email addresses for as low as $2 to fill a growing demand by hackers who use them for business email compromise and phishing attacks or initial access to networks.
Analysts at Israeli cyber-intelligence firm KELA have closely followed this trend, reporting at least 225,000 email accounts for sale on underground markets.
The largest webmail shops are Xleet and Lufix, claiming to offer access to over 100k breached corporate email accounts, with prices ranging between $2 and $30, if not more, for highly-desirable organizations.
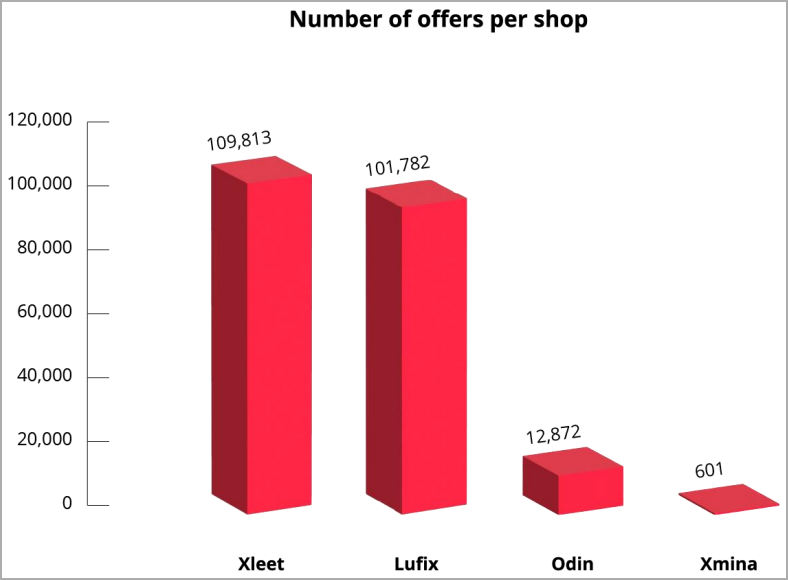
Webmail shop offers
Typically, these accounts were stolen via password cracking (brute-forcing) or credential stuffing, had their credentials stolen through phishing, or were bought from other cybercriminals.
Hackers use their access to corporate email accounts in targeted attacks like business email compromise (BEC), social engineering, spear-phishing, and deeper network infiltration.
Rise of webmail auto-shops
Sales of corporate email access have remained steady in the cybercrime space over the past couple of years, with threat actors on all major hacking forums selling email “combo lists” to access various firms.
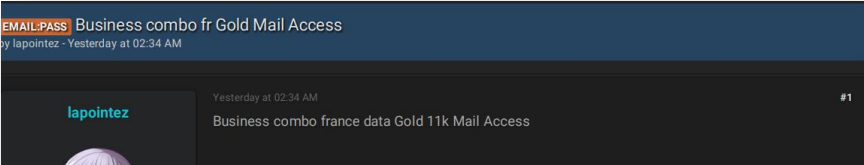
Combo list sold on 'Breached' forums
In a recent high-profile case, ransomware actor ‘Everest’ offered alleged access to email accounts of an aerospace manufacturing company for $15,000.
Both bulk and curated offers involve the tedious process of negotiating with the seller and taking a risk on the validity of the claims. At the same time, the demand for corporate emails continues to grow.
This has created the need for automated webmail shops like Xleet, Odin, Xmina, and Lufix, which allow cybercriminals to easily buy access to the email accounts of their choice.
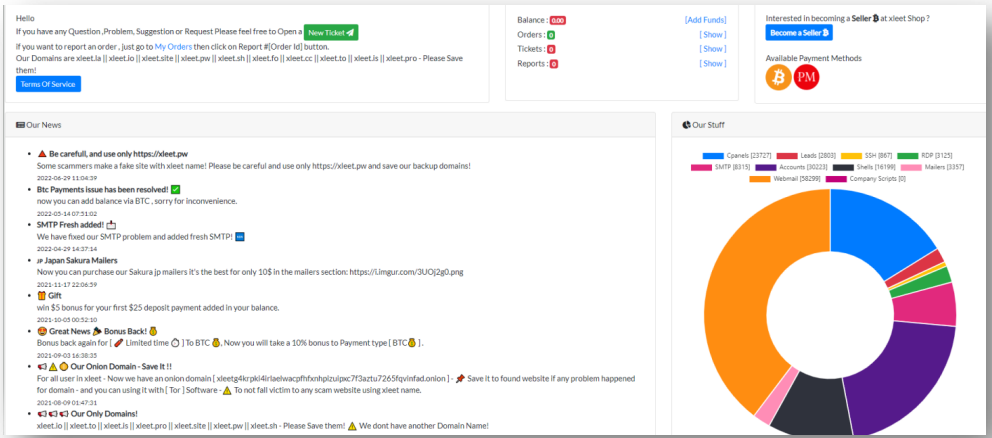
The main page of the Xleet shop
“Many of these shops provide advanced functions, such as “proofs” that webmail access indeed works,” explains KELA in the report.
“These proofs include performing a live check on the email to verify the access or showing a screenshot of the compromised account inbox.”
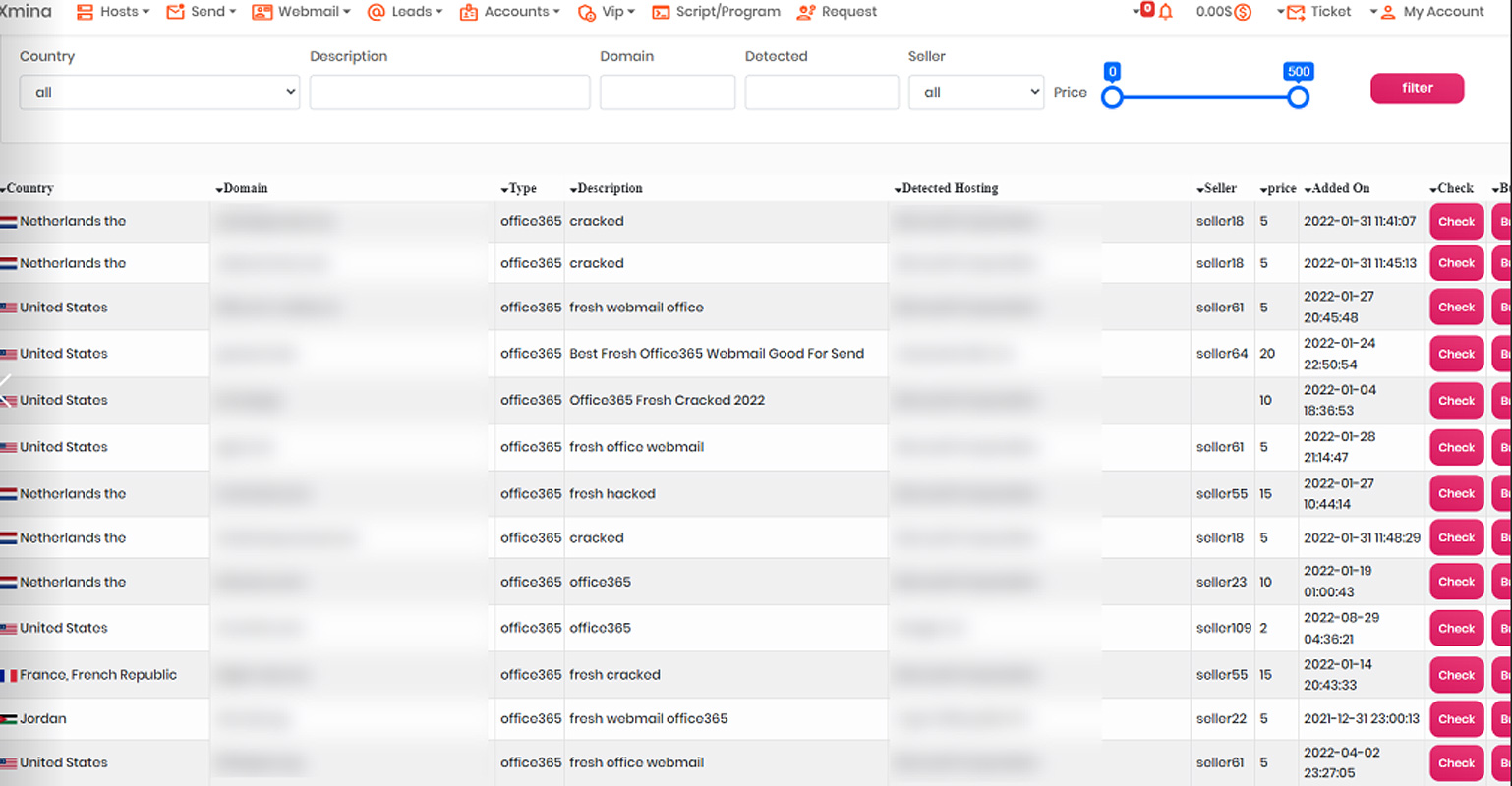
The checker system incorporated on all four shops
The most attractive offers are Office 365 accounts, which account for almost half of all listed webmail, followed by hosting providers like cPanel, GoDaddy, and Ionos.
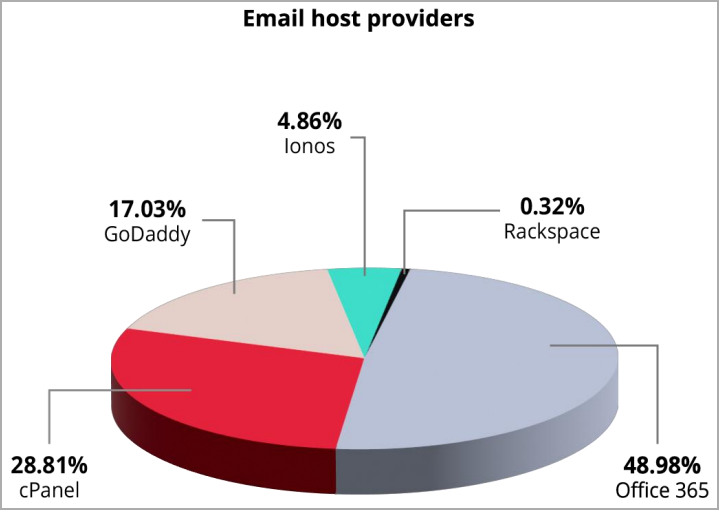
Providers of email accounts on offer
The sellers in these shops aren’t using aliases but hide behind a masking system assigning them numbers. Odin offers more details about the sellers, like the number of items sold, total sales figures, and user ratings.
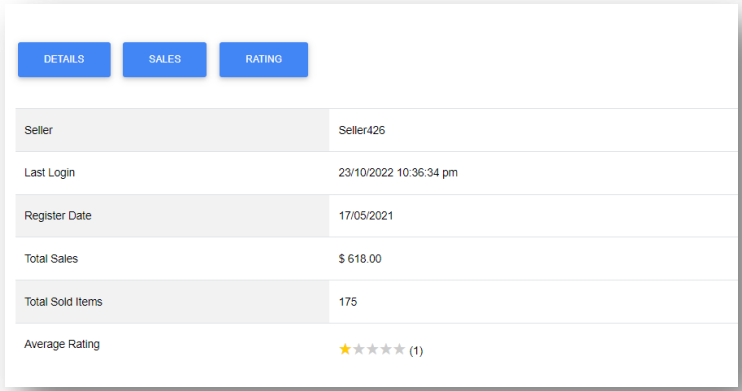
Seller details on Odin
Odin and Xleet also clarify how the webmails were sourced, with the categories including “hacked”, “cracked”, “logs”, or “created.” However, the majority (98%) in Xleet were either “hacked” or “cracked.”
“Logs” are email credentials stolen by info-stealing malware, while “created” are new email accounts that network intruders created on the breached firm using compromised administrator accounts.
The rise of these markets makes it imperative to enforce periodic password resets for all services and platforms to render compromised credentials useless.
Since most of the offered webmails are cracked or hacked, using strong (longer) passwords and training personnel to identify phishing emails would help reduce these threats significantly.

