Hackers are launching attacks against Palo Alto Networks PAN-OS firewalls by exploiting a recently fixed vulnerability (CVE-2025-0108) that allows bypassing authentication.
The security issue received a high-severity score and impacts the PAN-OS management web interface and allows an unauthenticated attacker on the network to bypass authentication and invoke certain PHP scripts, potentially compromising integrity and confidentiality.
In a
http://security.paloaltonetworks.com/CVE-2025-0108 on February 12, Palo Alto Networks urges admins to upgrade firewalls to the versions below to address the issue:
PAN-OS 11.0 is also impacted but the product reached the end of life (EoL) and Palo Alto Networks does not plan to release any fixes for it. Because of this, users are strongly recommended to upgrade to a supported release instead.
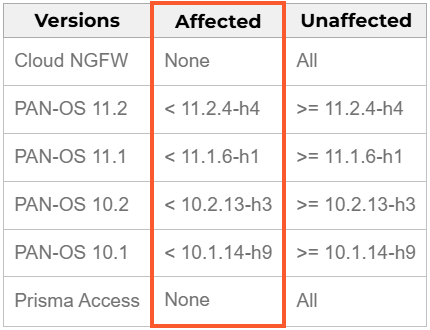
Affected PAN-OS versions
The vulnerability was discovered and reported to Palo Alto Networks by security researchers at Assetnote. They also published a write-up with
https://www.assetnote.io/resources/r...pass-in-pan-os when the patch was released.
The researchers demonstrated how the flaw could be leveraged to extract sensitive system data, retrieve firewall configurations, or potentially manipulate certain settings within PAN-OS.
The exploit leverages a path confusion between Nginx and Apache in PAN-OS that allows bypassing authentication.
Attackers with network access to the management interface can leverage this to gather intelligence for further attacks or to weaken security defenses by modifying accessible settings.

Exploitation workflow
Threat monitoring platform GreyNoise logged
http://www.greynoise.io/blog/greynoi...-cve-2025-0108 targeting unpatched PAN-OS firewalls.
The attacks started on February 13, at 17:00 UTC, and appear to originate from several IP addresses, potentially indicating exploitation efforts from distinct threat actors.
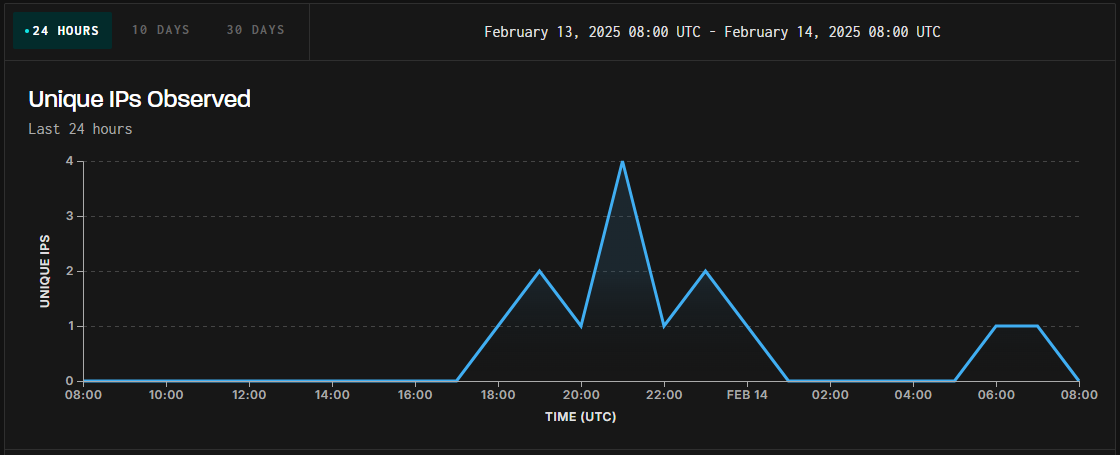
Malicious activity in the wild
Regarding the exposure of vulnerable devices online, Macnica researcher Yutaka Sejiyama told BleepingComputer that there are currently over 4,400 PAN-OS devices exposing their management interface online.
To defend against the ongoing exploitation activity, which, considering that the PoC is public, is very likely to culminate in the following days, it is recommended to apply the available patches and restrict access to firewall management interfaces.
https://www.bleepingcomputer.com/new...tworks-pan-os/

