Cyble Research and Intelligence Labs (CRIL) discovered a new Android banking trojan that uses an overlay attack to target over 750 applications, including banking, finance, cryptocurrency, payment, social media, and e-commerce applications, across multiple regions.
While the malware mainly utilizes overlay attacks to steal credentials, it also carries out various other malicious actions. It is capable of recording and remotely controlling the screen, enabling attackers to monitor and manipulate the device. Additionally, it employs lock-grabbing techniques, keylogging, and intercepting SMS messages.
The analyzed samples indicate the presence of a newly discovered banking trojan, which we are internally tracking as “TsarBot,” a name chosen due to the threat actor’s suspected Russian origin. During our investigation, we identified multiple log entries in Russian within the malicious application, suggesting that a Russian-speaking threat actor likely developed the malware.

Figure 1 – Logs in the Russian Language
TsarBot has been observed spreading through a phishing site that impersonates the official Photon Sol website. The phishing site deceptively offers a download option for an application to start trading, whereas the legitimate website lacks such an option.
The following phishing sites impersonate legitimate entities and distribute dropper applications that, once installed on the targeted device, will deploy TsarBot.
- hxxps://cashraven[.]online

Figure 2 – Phishing site distributing TsarBot

Figure 3 – Phishing site distributing TsarBot
Technical Details
As previously mentioned, the phishing site delivers a dropper application that stores the TsarBot APK file, implant.apk, in the “res/raw” folder. The dropper utilizes a session-based package installer to deploy the TsarBot malware on the device.

Figure 4 – Dropper installing TsarBot
TsarBot conceals itself as the Google Play Service app and does not display a launcher icon. Upon installation, it presents a fake Google Play Service update page, prompting the user to enable Accessibility services.

Figure 5 – Malware prompting victims to enable Accessibility services
WebSocket Connection
After the victim enables the Accessibility service, the malware establishes a socket connection with the C&C server “hxxp://95.181[.]173.76” using four different ports listed below:
- 9001 – To receive commands
- 9002 – To send captured screen content
- 9004 – To receive different sets of commands
- 9030 – To send data to the server
TsarBot can receive various commands from the server, primarily focused on-screen control, enabling it to carry out on-device fraud.
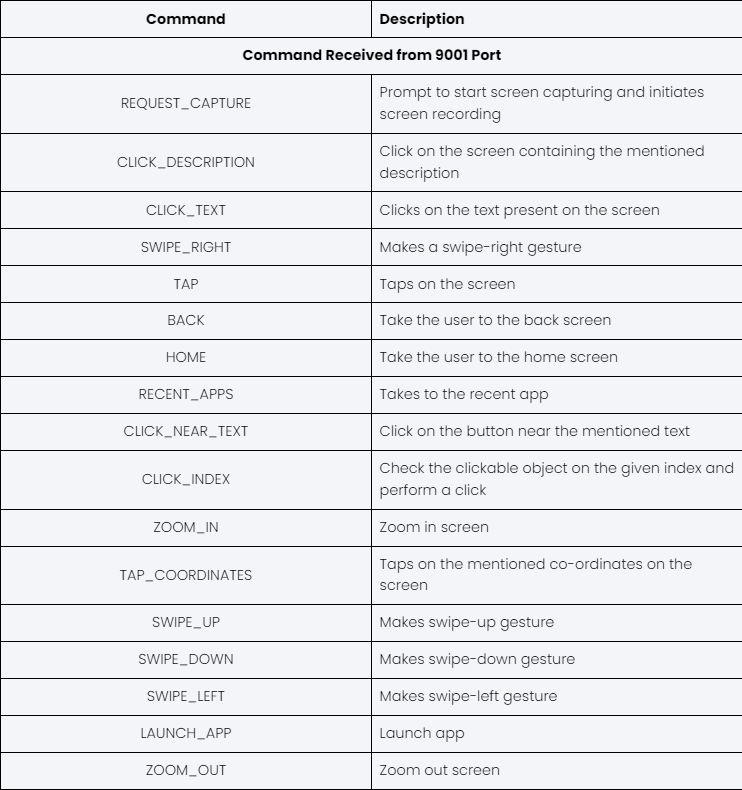
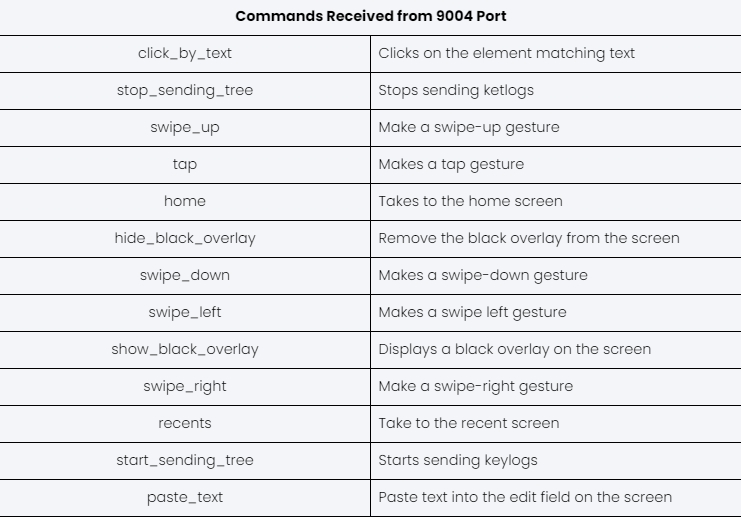 Screen Recording
Screen Recording
As outlined in the command table, when TsarBot receives the “REQUEST_CAPTURE” command, it prompts the user to enable screen capture permissions. Once granted, the malware initiates the screen capture service, transmitting the captured screen content to the C&C server via a WebSocket connection on port 9002.

Figure 6 – Screen capture service
By capturing screen content and executing server-issued screen control commands, TsarBot can carry out fraudulent transactions on the targeted device by concealing this fraud activity with a black overlay screen.
Lock Grabber
TsarBot incorporates the LockTypeDetector feature to determine the device’s lock type using the Accessibility service. It detects specific on-screen text or descriptions, such as “PIN area,” “Device password,” or a pattern, to identify the lock method. Once identified, it saves the lock type status for future use in lock-grabbing operations.

Figure 7 – Lock type detection code
When TsarBot receives the “USER_PRESENT” action for the first time, it loads a fake lock screen based on the detected lock type from “hxxps://xdjhgfgjh[.]run/injects/htmlPIN/android.PinCode.html” and captures the user’s lock password, PIN, or pattern.

Figure 8 – Malware loading fake lock screen
Overlay Attack
TsarBot connects to the URL “hxxps://xdjhgfgjh[.]run/injects/ServiceName.txt“ to retrieve a list of targeted application package names. Most of these belong to banking apps from various regions, including France, Poland, the UK, India, the UAE, and Australia. The remaining package names are associated with e-commerce, social media, messaging apps, cryptocurrency, and other categories.

Figure 9 – TsarBot receiving the target application package names
TsarBot collects the installed applications on the infected device and compares them against the package names received from the server, maintaining a target list for overlay attacks.

Figure 10 – Malware comparing the installed application package names with the target list received from the server
When the victim interacts with an application, TsarBot checks its package name against the maintained target list. If the application is found in the targeted list, it then retrieves the corresponding injection page from “hxxps://xdjhgfgjh[.]run/injects/html/{packagename}.html“ and loads it into a WebView.

Figure 11 – Creating an overlay window on top of the targeted application
The injection page mimics a legitimate application, tricking users into entering sensitive information such as net banking credentials, log in details, and credit card information. The figure below shows the injection pages for one of the target applications.

Figure 12 – Injection page for Indian Bank prompting to enter login and credit card details
The data entered into the injection phishing pages is sent to the C&C server over port 9030. After transmitting the stolen sensitive information, TsarBot removes the targeted application’s package name from the list to prevent the overlay from being triggered again for the same app.

Figure 13 – Sends collected login and credit card information from overlay activity to the C&C server

Figure 14 – Removing application package name from target list
The image below shows the injection pages used by TsarBot to trick the victims into submitting sensitive information while attempting to access genuine applications.

Figure 15 – Injection pages for different applications
Conclusion
TsarBot is yet another addition to the growing list of Android banking trojans, relying on familiar yet effective tactics such as overlay attacks, screen recording, and lock grabbing. By abusing Accessibility services and WebSocket communication, it enables on-device fraud while maintaining a low profile. With its ability to target over 750 applications across multiple sectors, TsarBot underscores the persistent threat posed by banking malware. Users should exercise caution when installing apps, avoid untrusted sources, and remain vigilant against phishing sites distributing such threats.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Download and install software exclusively from official application stores, such as the Google Play Store or the iOS App Store.
- Utilize a reputable antivirus and internet security software package on all connected devices, including personal computers, laptops, and mobile devices.
- Implement strong passwords and enforce multi-factor authentication wherever feasible.
- Activate biometric security features, such as fingerprint or facial recognition, for unlocking mobile devices when available.
- Exercise caution while opening links that have been sent via SMS or emails on your mobile device.
- Ensure that Google Play Protect is enabled on Android devices.
- Be judicious when granting permissions to applications.
- Maintain updated versions of your devices, operating systems, and applications.
https://cyble.com/blog/tsarbot-using...g-bfsi-sector/



