A new Android spyware named 'KoSpy' is linked to North Korean threat actors who have infiltrated Google Play and third-party app store APKPure through at least five malicious apps.
According to Lookout researchers, the spyware is attributed to the North Korean threat group APT37 (aka 'ScarCruft'). The campaign has been active since March 2022, with the threat actors actively developing the malware based on newer samples.
The spyware campaign primarily targets Korean and English-speaking users by disguising itself as file managers, security tools, and software updaters.
The five apps Lookout identified are 휴대폰 관리자 (Phone Manager), File Manager (com.file.exploer), 스마트 관리자 (Smart Manager), 카카오 보안 (Kakao Security), and Software Update Utility.
Malicious app on Google Play
The malicious apps offer at least some of the promised functionality but load the KoSpy spyware in the background.
The only exception is Kakao Security, which only displays a fake system window while requesting access to risky permissions.
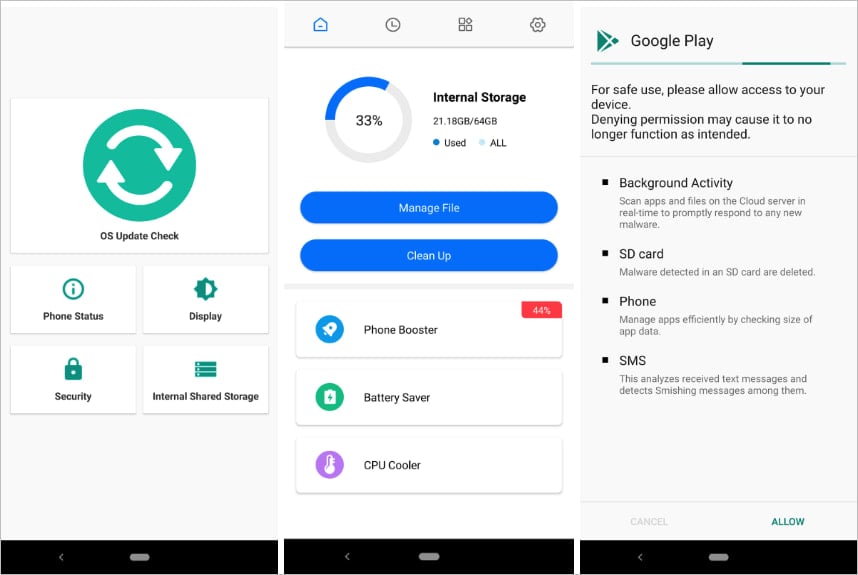
Interface of KoSpy apps
The campaign was attributed to
https://www.bleepingcomputer.com/new...missile-maker/ based on IP addresses previously linked to North Korean operations, domains that facilitated the distribution of
https://www.bleepingcomputer.com/new...i-rat-malware/, and infrastructure that overlaps with APT43, another DPRK-sponsored threat group.
KoSpy details
Once active on the device, KoSpy retrieves an encrypted configuration file from a Firebase Firestore database to evade detection.
Next, it connects to the actual command and control (C2) server and runs checks to ensure it's not running in an emulator. The malware can retrieve updated settings from the C2, additional payloads to execute, and be activated/deactivated dynamically via an "on/off" switch.
KoSpy's data collection capabilities are:
- SMS and call logs interception
- Tracks victim's GPS location in real-time
- Reads and exfiltrates files from local storage
- Uses the device's microphone to record audio
- Uses the device's camera to capture photos and videos
- Captures screenshots of the device display
- Records keystrokes via Android Accessibility Services
Each app uses a separate Firebase project and C2 server for the data exfiltration, which is encrypted with a hardcoded AES key prior to transmission.
Although the spyware apps have now been removed from both Google Play and APKPure, users will need to manually uninstall them and scan them with security tools to uproot any remnants of the infection from their devices. In critical cases, a factory reset is recommended.
Google Play Protect is also able to block known malicious apps, so enabling it on up-to-date Android devices can help protect against KoSpy.
A Google spokesperson confirmed to BleepingComputer that all the KoSpy apps identified by Lookout have been removed from Google Play and that the corresponding Firebase projects have also been taken down.
"The use of regional language suggests this was intended as targeted malware. Before any user installations, the latest malware sample discovered in March 2024 was removed from Google Play," Google told BleepingComputer.
"Google Play Protect automatically protects Android users from known versions of this malware on devices with Google Play Services, even when apps come from sources outside of Play."
https://www.bleepingcomputer.com/new...o-google-play/

