New malicious NPM packages have been discovered that install the njRAT remote access trojan that allows hackers to gain control over a computer.
NPM is a JavaScript package manager that allows developers and users to download packages and integrate them into their projects.
As NPM is an open ecosystem, anyone can upload a new package without being reviewed or scanned for malware. While this environment has led to a repository of 1 million rich and diverse packages, it also makes it easy for threat actors to upload malicious packages.
Malicious NPMs install njRAT
Today, open-source security firm Sonatype discovered malicious NPM packages masquerading as a legitimate tool to make databases out of JSON files.
These packages were called 'jdb.js' and 'db-json.js' and have been removed by NPM, but as you can see from a screenshot below, they look like harmless packages that could be used to add new functionality to a project.
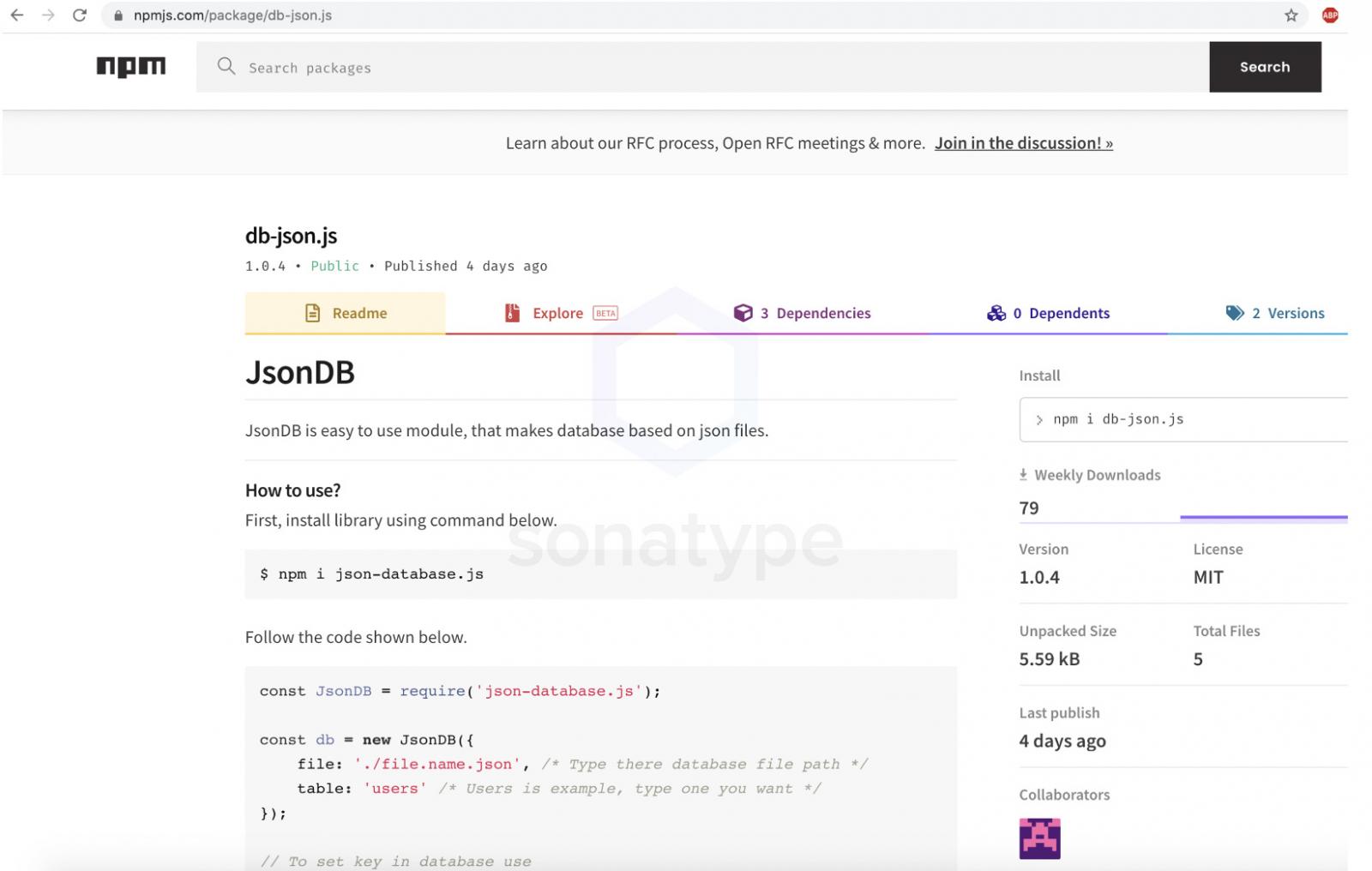
JsonDB (db-json.js) package on NPM
As you can see from the package.json file for the db-json.js package, it has another package called 'jdb.js' as a dependency. The package.json file causes NPM to automatically install that package as well when installing the db-json.js package.
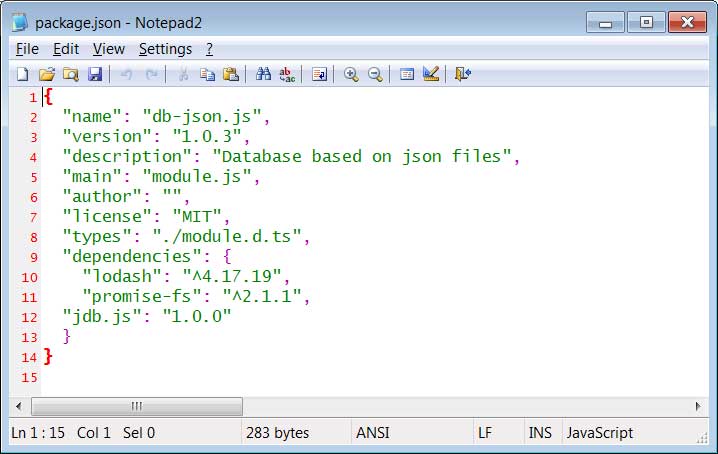
Package.json for db-json
This jdb.js package includes a module.js, package.json, and a patch.exe executable, as shown below. When installed, NPM will automatically execute the module.js as it is set to launch automatically on install.
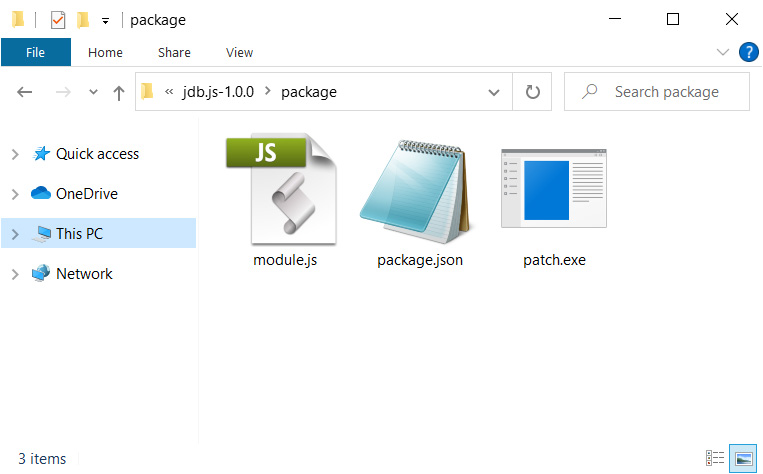
jdb package contents
This JS script, shown below, is heavily obfuscated but will launch the patch.exe executable, which is the njRAT malware.
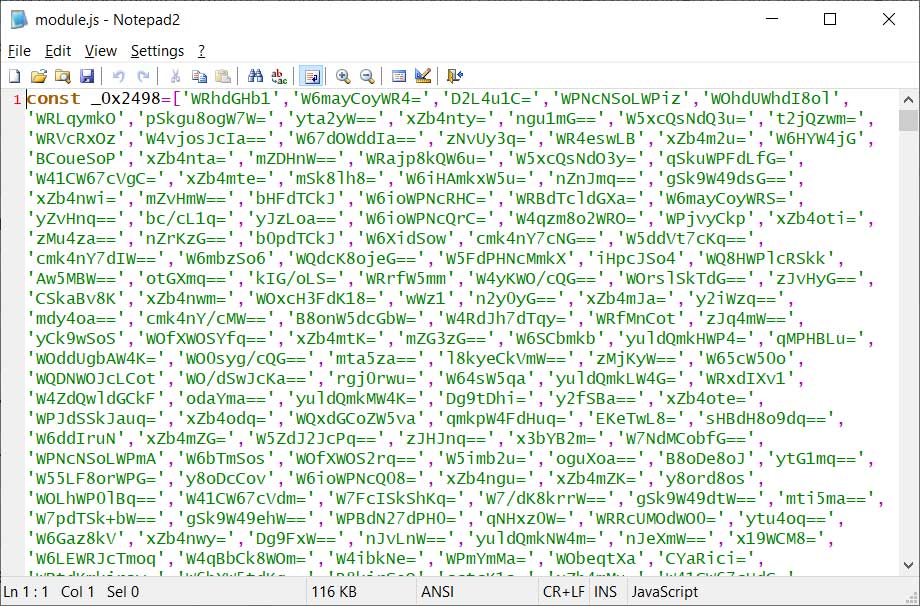
Obfuscated JavaScript file
When installed, njRAT gives the threat actor full remote access to a victim's computer, where they can perform the following malicious behavior:
- Modify the Windows Registry
- Create and delete files
- Upload files
- Execute commands
- Get information about the computer
- Take control over the computer
- Log keystrokes
- Steal passwords
- Kill processes
- Take screenshots
Below you can see a small snippet of source code showing some commands that can be sent by the threat actor via njRAT.
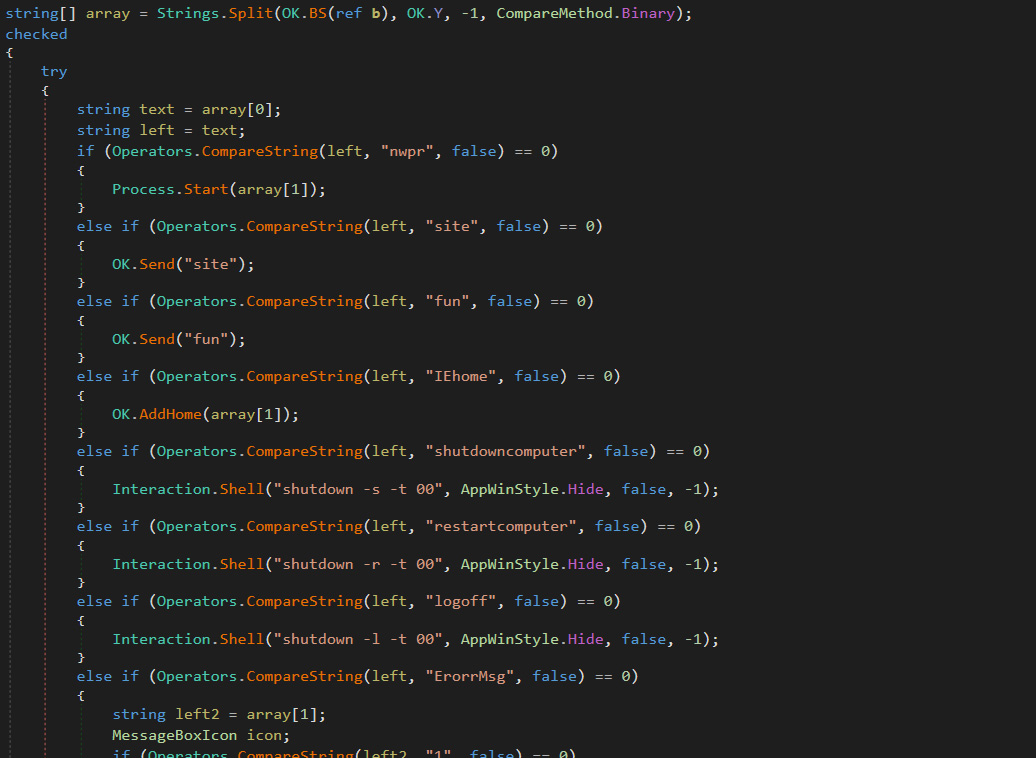
njRAT decompiled source code
Each package was downloaded about a hundred times each, but Sonatype's Ax Sharma told BleepingComputer that they believe they caught the malicious NPMs before they could be put to full use.
Over the past year, it has become increasingly common to find NPM packages that install malware or perform malicious behavior.
Recently, NPM removed malicious packages called 'fallguy' and 'discord.dll' after discovering that they were used to steal Discord tokens and browser information from Google Chrome, Brave Browser, Opera, and Yandex Browser.
As it is becoming common for malicious NPM projects to utilize names similar to legitimate projects, developers must pay close attention to the packages they integrate into their projects.
